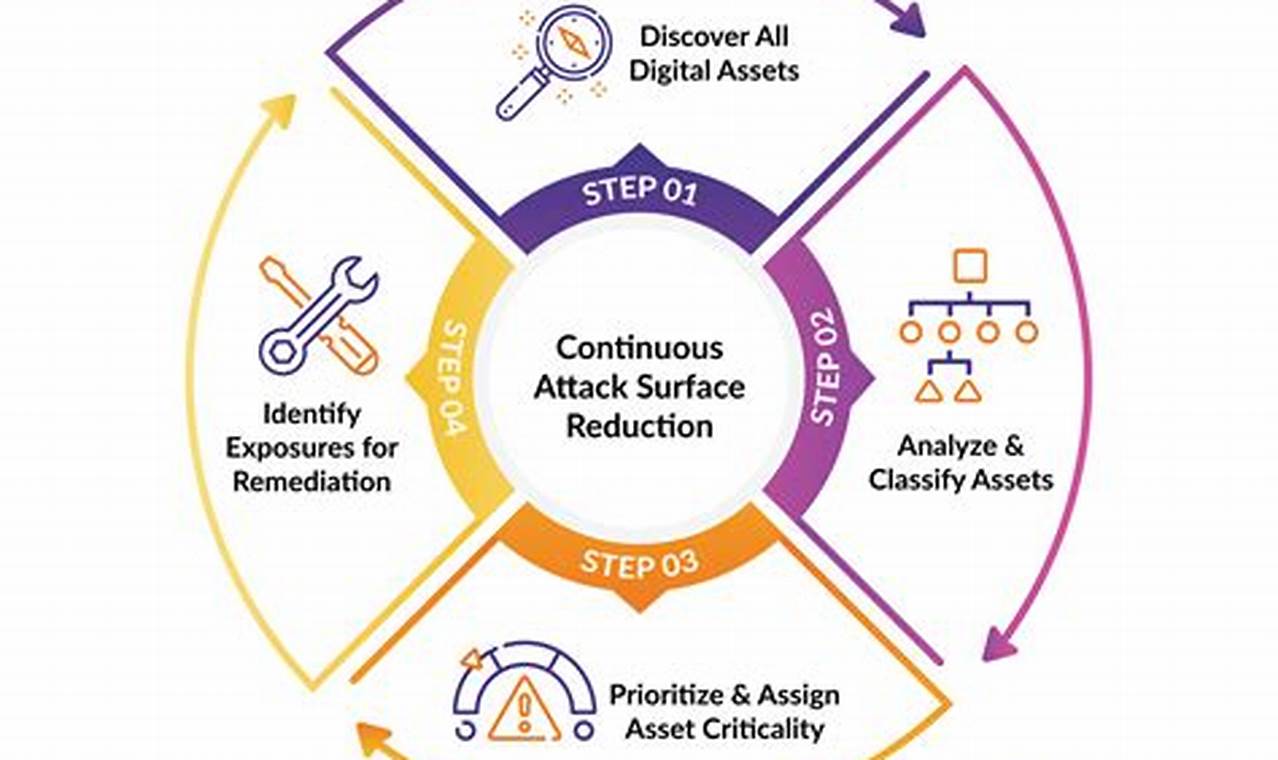
Attack surface reduction refers to the intentional reduction of the number of potential entry points that an attacker can use to access a computer system or network. This is typically achieved through a combination of security measures, such as patching software, implementing firewalls, and using intrusion detection systems. By reducing the attack surface, organizations can make it more difficult for attackers to gain access to their systems and data.
Attack surface reduction is an important part of any comprehensive cybersecurity strategy. By reducing the number of potential entry points for attackers, organizations can make it more difficult for them to compromise their systems. This can help to protect sensitive data, prevent financial losses, and maintain the reputation of the organization.
In recent years, there has been a growing focus on attack surface reduction as organizations have become more aware of the risks associated with cyberattacks. This is due in part to the increasing sophistication of attackers and the growing number of connected devices. As a result, organizations are increasingly investing in attack surface reduction measures to protect their systems and data.
Attack surface reduction
Attack surface reduction involves identifying and mitigating potential entry points for attackers to exploit. It encompasses diverse key aspects that contribute to a robust cybersecurity posture.
- Vulnerability management: Patching software and systems to address known vulnerabilities.
- Configuration management: Ensuring secure system configurations to minimize attack vectors.
- Network segmentation: Isolating network segments to limit the spread of attacks.
- Firewall implementation: Deploying firewalls to block unauthorized access to systems.
- Intrusion detection and prevention: Monitoring networks for suspicious activity and preventing attacks.
- Access control: Restricting access to systems and data based on user roles and permissions.
- Security awareness training: Educating users on security best practices to prevent social engineering attacks.
- Continuous monitoring: Regularly reviewing and updating security measures to address evolving threats.
These key aspects work synergistically to reduce the attack surface, making it more challenging for attackers to compromise systems and data. By implementing a comprehensive attack surface reduction strategy, organizations can significantly enhance their cybersecurity posture and protect against a wide range of threats.
Vulnerability management
Vulnerability management, which involves patching software and systems to address known vulnerabilities, plays a critical role in attack surface reduction. Known vulnerabilities are weaknesses in software or systems that can be exploited by attackers to gain unauthorized access or execute malicious code. By promptly patching these vulnerabilities, organizations can significantly reduce the attack surface and make it more difficult for attackers to compromise their systems.
For instance, the widespread WannaCry ransomware attack in 2017 exploited a vulnerability in Microsoft’s Server Message Block (SMB) protocol. Organizations that had not applied the available patch were vulnerable to this attack, which encrypted files and demanded ransom payments. This incident highlights the importance of timely vulnerability management in reducing the attack surface and preventing successful cyberattacks.
In addition to patching software, vulnerability management also involves updating firmware and hardware components. By keeping all system components up to date, organizations can minimize the number of potential entry points for attackers and enhance their overall security posture.
Configuration management
Configuration management is the practice of ensuring that systems are configured securely to minimize the risk of attack. This involves setting up systems in a way that reduces the number of potential entry points for attackers and makes it more difficult for them to exploit vulnerabilities.
- Default settings: Many systems come with default settings that are not always secure. By changing these settings to more secure values, organizations can reduce their attack surface and make it more difficult for attackers to compromise their systems.
- Unnecessary services: Many systems have services running that are not necessary for the system to function. By disabling these services, organizations can reduce the number of potential attack vectors and make it more difficult for attackers to gain access to their systems.
- Vulnerable software: Keeping software up to date is important for security, as updates often include patches for vulnerabilities. By ensuring that all software is up to date, organizations can reduce their attack surface and make it more difficult for attackers to exploit vulnerabilities.
- Strong passwords: Using strong passwords is essential for protecting systems from unauthorized access. By requiring users to use strong passwords and changing passwords regularly, organizations can reduce the risk of attackers gaining access to their systems.
Configuration management is an important part of attack surface reduction. By ensuring that systems are configured securely, organizations can make it more difficult for attackers to compromise their systems and data.
Network segmentation
In the realm of cybersecurity, network segmentation plays a pivotal role in reducing the attack surface and mitigating the impact of cyber threats. By partitioning a network into distinct segments, organizations can isolate critical assets and resources, thereby limiting the potential spread and impact of malicious activity.
- Isolation of Critical Assets: Network segmentation allows organizations to isolate critical assets, such as servers, databases, and other sensitive resources, from the rest of the network. This isolation reduces the risk of attackers gaining access to these critical assets and compromising sensitive data or disrupting essential services.
- Containment of Breaches: In the event of a security breach, network segmentation can help contain the damage by preventing the spread of malware or unauthorized access to other segments of the network. By isolating infected devices or segments, organizations can minimize the impact of the breach and facilitate faster recovery.
- Enhanced Security Monitoring: Network segmentation simplifies security monitoring by dividing the network into smaller, more manageable segments. This enables organizations to focus their monitoring efforts on specific segments, allowing for more effective detection and response to security incidents.
- Compliance and Regulatory Adherence: Network segmentation is often a requirement for compliance with industry regulations and standards, such as PCI DSS and HIPAA. By segmenting their networks, organizations can demonstrate that they have taken appropriate steps to protect sensitive data and comply with regulatory mandates.
In summary, network segmentation is a critical component of attack surface reduction. By isolating network segments, organizations can reduce the risk of successful cyberattacks, minimize the impact of security breaches, and enhance their overall security posture.
Firewall implementation
Firewalls are network security devices that monitor and control incoming and outgoing network traffic based on predetermined security rules. Their primary function is to block unauthorized access to systems and networks, thereby reducing the attack surface and enhancing overall security.
-
Facet 1: Perimeter Defense
Firewalls act as a defensive barrier between a network and the external world, blocking unauthorized access attempts from the internet. By establishing a perimeter around the network, firewalls restrict access to authorized users and prevent malicious actors from gaining entry. -
Facet 2: Access Control
Firewalls implement access control policies that define which types of traffic are allowed to enter or leave the network. These policies can be based on IP addresses, port numbers, protocols, or other criteria. By controlling access, firewalls prevent unauthorized users from accessing sensitive resources or launching attacks. -
Facet 3: Intrusion Prevention
Firewalls can be configured to detect and block malicious traffic, such as malware, phishing attempts, and denial-of-service attacks. By analyzing network traffic patterns and identifying suspicious behavior, firewalls prevent these threats from reaching internal systems and compromising data or disrupting operations. -
Facet 4: Logging and Monitoring
Firewalls can log and monitor network traffic, providing valuable insights into security events and potential threats. These logs can be analyzed to identify trends, detect suspicious activity, and improve the overall security posture of the network.
In summary, firewall implementation plays a vital role in attack surface reduction by blocking unauthorized access to systems, implementing access control policies, preventing intrusions, and providing logging and monitoring capabilities. By deploying firewalls, organizations can significantly reduce the risk of successful cyberattacks and protect their sensitive data and systems.
Intrusion detection and prevention
Intrusion detection and prevention (IDP) systems are an essential component of attack surface reduction. They monitor network traffic for suspicious activity and can take action to prevent attacks from succeeding. This is important because it helps to reduce the number of potential entry points for attackers and makes it more difficult for them to compromise systems.
IDP systems work by analyzing network traffic for patterns that are indicative of an attack. For example, they may look for traffic that is coming from unusual sources, or that is attempting to exploit known vulnerabilities. If an IDP system detects suspicious activity, it can take action to block the traffic or alert security personnel.
There are a number of different types of IDP systems available, each with its own strengths and weaknesses. Some IDP systems are based on signature detection, which means that they look for specific patterns of traffic that are known to be associated with attacks. Other IDP systems use anomaly detection, which means that they look for traffic that deviates from the normal pattern of activity on the network.
IDP systems are an important part of any comprehensive security strategy. They can help to reduce the risk of successful attacks and protect sensitive data and systems.
Access control
Access control is a critical component of attack surface reduction. By restricting access to systems and data based on user roles and permissions, organizations can significantly reduce the number of potential entry points for attackers and make it more difficult for them to compromise sensitive information.
For example, consider an organization that has a file server that stores sensitive financial data. If all users on the network have access to this file server, then an attacker who gains access to any one user’s account will also have access to the financial data. However, if the organization implements access control and only grants access to the file server to a limited number of users who have a legitimate need to access the data, then the attacker will not be able to access the financial data even if they gain access to a user’s account.
Access control can also be used to prevent unauthorized users from making changes to systems or data. For example, if a user does not have permission to modify a system file, then they will not be able to make changes to that file, even if they have access to the system. This can help to prevent attackers from making unauthorized changes to systems or data that could compromise the security of the organization.
Implementing access control is an essential part of any comprehensive attack surface reduction strategy. By restricting access to systems and data based on user roles and permissions, organizations can significantly reduce the risk of a successful attack and protect their sensitive information.
Security awareness training
Security awareness training is an essential component of any comprehensive attack surface reduction strategy. Social engineering attacks rely on tricking users into giving up sensitive information or access to systems, and security awareness training can help users to recognize and avoid these attacks.
-
Facet 1: Understanding Social Engineering Techniques
Security awareness training can help users to understand the different social engineering techniques that attackers use, such as phishing, spear phishing, and pretexting. By understanding these techniques, users can be more vigilant and less likely to fall victim to them. -
Facet 2: Recognizing Suspicious Emails and Websites
Security awareness training can also help users to recognize suspicious emails and websites. Attackers often use phishing emails and websites to trick users into giving up their passwords or other sensitive information. By learning to recognize the signs of phishing, users can avoid falling victim to these attacks. -
Facet 3: Protecting Passwords and Other Sensitive Information
Security awareness training can also teach users how to protect their passwords and other sensitive information. Users should never share their passwords with anyone, and they should use strong passwords that are difficult to guess. They should also be careful about what information they share online, and they should never share sensitive information over email or social media. -
Facet 4: Reporting Suspicious Activity
Finally, security awareness training can also teach users how to report suspicious activity. If a user receives a suspicious email or visits a suspicious website, they should report it to their IT department or security team. By reporting suspicious activity, users can help to protect their organization from social engineering attacks.
Security awareness training is an essential part of any attack surface reduction strategy. By educating users on security best practices, organizations can reduce the risk of social engineering attacks and protect their sensitive information and systems.
Continuous monitoring
Continuous monitoring is an essential aspect of attack surface reduction. By regularly reviewing and updating security measures, organizations can identify and address vulnerabilities before they can be exploited by attackers. This is critical because the threat landscape is constantly evolving, and new vulnerabilities are emerging all the time.
-
Facet 1: Vulnerability Management
Continuous monitoring includes regularly scanning systems for vulnerabilities and patching any that are found. This helps to reduce the number of potential entry points for attackers and make it more difficult for them to compromise systems. -
Facet 2: Security Configuration Management
Continuous monitoring also involves regularly reviewing and updating security configurations. This ensures that systems are configured securely and that there are no weak points that could be exploited by attackers. -
Facet 3: Intrusion Detection and Prevention
Continuous monitoring can also involve using intrusion detection and prevention systems to monitor network traffic for suspicious activity. These systems can detect and block attacks in real time, helping to prevent them from reaching their targets. -
Facet 4: Security Logging and Analysis
Continuous monitoring also involves regularly reviewing security logs and analyzing them for suspicious activity. This can help to identify trends and patterns that could indicate an impending attack.
By implementing continuous monitoring, organizations can significantly reduce their attack surface and make it more difficult for attackers to compromise their systems and data.
Attack Surface Reduction FAQs
This section provides answers to frequently asked questions about attack surface reduction, a critical aspect of cybersecurity.
Question 1: What is attack surface reduction?
Attack surface reduction refers to the strategies and techniques employed to minimize the number of potential entry points that attackers can exploit to access a computer system or network. It involves identifying and mitigating vulnerabilities, implementing security controls, and continuously monitoring and updating security measures.
Question 2: Why is attack surface reduction important?
Attack surface reduction helps organizations protect their systems and data from cyberattacks by proactively reducing the number of potential vulnerabilities that attackers can target. A smaller attack surface makes it more difficult for attackers to gain unauthorized access and compromise sensitive information.
Question 3: What are some common attack surface reduction techniques?
Common attack surface reduction techniques include vulnerability management (patching software and systems), configuration management (securing system settings), network segmentation (isolating network segments), firewall implementation (blocking unauthorized access), intrusion detection and prevention (monitoring for suspicious activity), access control (restricting access based on permissions), security awareness training (educating users on security best practices), and continuous monitoring (regularly reviewing and updating security measures).
Question 4: How can organizations implement attack surface reduction?
Organizations can implement attack surface reduction by conducting regular security assessments to identify vulnerabilities, implementing security controls such as firewalls and intrusion detection systems, providing security awareness training to employees, and continuously monitoring their systems and networks for suspicious activity.
Question 5: What are the benefits of attack surface reduction?
Attack surface reduction offers several benefits, including reduced risk of cyberattacks, enhanced data protection, improved regulatory compliance, and increased customer trust.
Question 6: How can organizations measure the effectiveness of their attack surface reduction efforts?
Organizations can measure the effectiveness of their attack surface reduction efforts by tracking metrics such as the number of vulnerabilities identified and patched, the number of security incidents detected and prevented, and the overall improvement in their security posture.
In summary, attack surface reduction is a crucial component of cybersecurity that helps organizations protect their systems and data from cyberattacks by reducing the number of potential entry points for attackers. Implementing a comprehensive attack surface reduction strategy can significantly enhance an organization’s security posture and mitigate the risks associated with cyber threats.
Transition to the next article section: This concludes the FAQs on attack surface reduction. For further information and guidance on implementing effective attack surface reduction measures, please refer to the following resources:
Attack Surface Reduction Tips
Implementing a robust attack surface reduction strategy is essential for organizations seeking to protect their systems and data from cyberattacks. Here are some practical tips to enhance your attack surface reduction efforts:
Tip 1: Prioritize Vulnerability Management
Regularly scan your systems for vulnerabilities and promptly apply patches to address identified weaknesses. This proactive approach significantly reduces the number of potential entry points that attackers can exploit.
Tip 2: Implement Network Segmentation
Divide your network into isolated segments to limit the spread of potential attacks. This prevents attackers from compromising multiple systems or accessing critical assets if they breach one segment.
Tip 3: Enforce Strong Access Controls
Implement access controls to restrict access to systems and data based on user roles and permissions. This ensures that only authorized individuals have access to sensitive information, reducing the risk of unauthorized access.
Tip 4: Implement Intrusion Detection and Prevention Systems
Deploy intrusion detection and prevention systems to monitor network traffic for suspicious activity and prevent potential attacks. These systems can detect and block malicious traffic in real-time, providing an additional layer of protection.
Tip 5: Provide Security Awareness Training
Educate your employees on security best practices to prevent social engineering attacks. Train them to recognize phishing attempts, protect sensitive information, and report suspicious activity, empowering them to contribute to the organization’s overall security posture.
Tip 6: Implement Continuous Monitoring
Regularly review and update your security measures to address evolving threats. Monitor security logs, conduct security assessments, and implement necessary changes to maintain a strong security posture.
By following these tips, organizations can effectively reduce their attack surface and mitigate the risk of cyberattacks. Implementing a comprehensive attack surface reduction strategy is a crucial step towards protecting critical assets, maintaining data integrity, and ensuring business continuity.
Attack Surface Reduction
In the ever-evolving landscape of cybersecurity, attack surface reduction has emerged as a crucial strategy for organizations to protect their systems and data from cyber threats. This comprehensive approach involves identifying and mitigating potential entry points for attackers, thereby reducing the risk of successful breaches.
To effectively implement attack surface reduction, organizations must prioritize vulnerability management, implement network segmentation, enforce strong access controls, and deploy intrusion detection and prevention systems. Additionally, providing security awareness training to employees and implementing continuous monitoring are essential to maintaining a robust security posture.
By embracing attack surface reduction strategies, organizations can significantly enhance their cybersecurity resilience. This proactive approach reduces the number of potential vulnerabilities that attackers can exploit, making it more difficult for them to compromise systems and access sensitive information. As the threat landscape continues to evolve, attack surface reduction will remain a cornerstone of effective cybersecurity practices, enabling organizations to protect their critical assets and maintain business continuity.
Youtube Video: