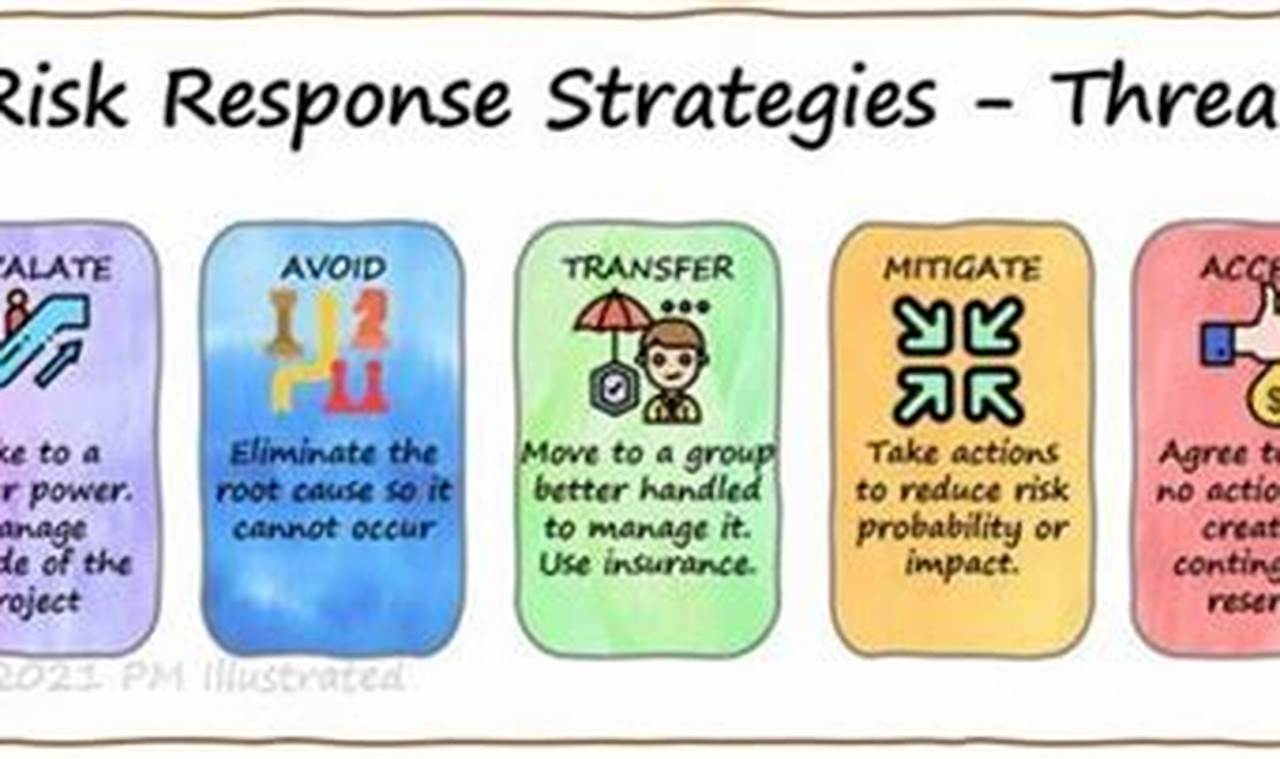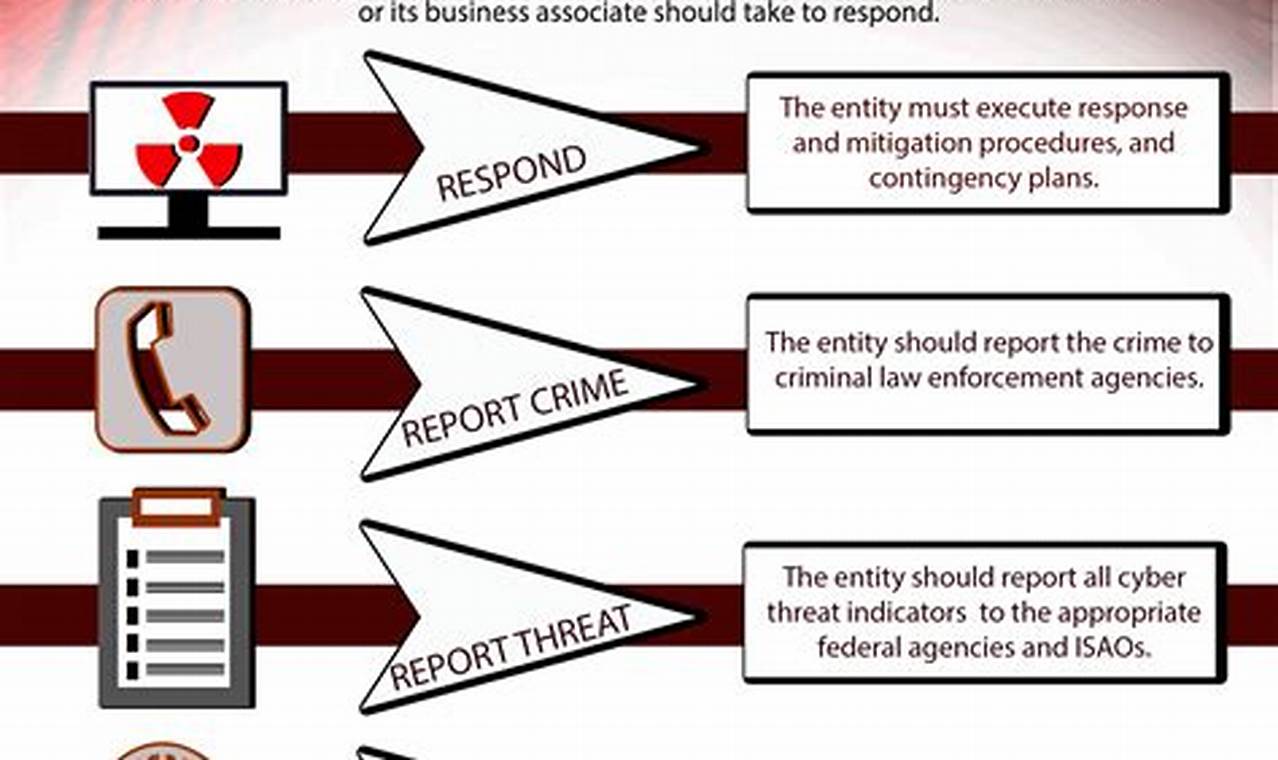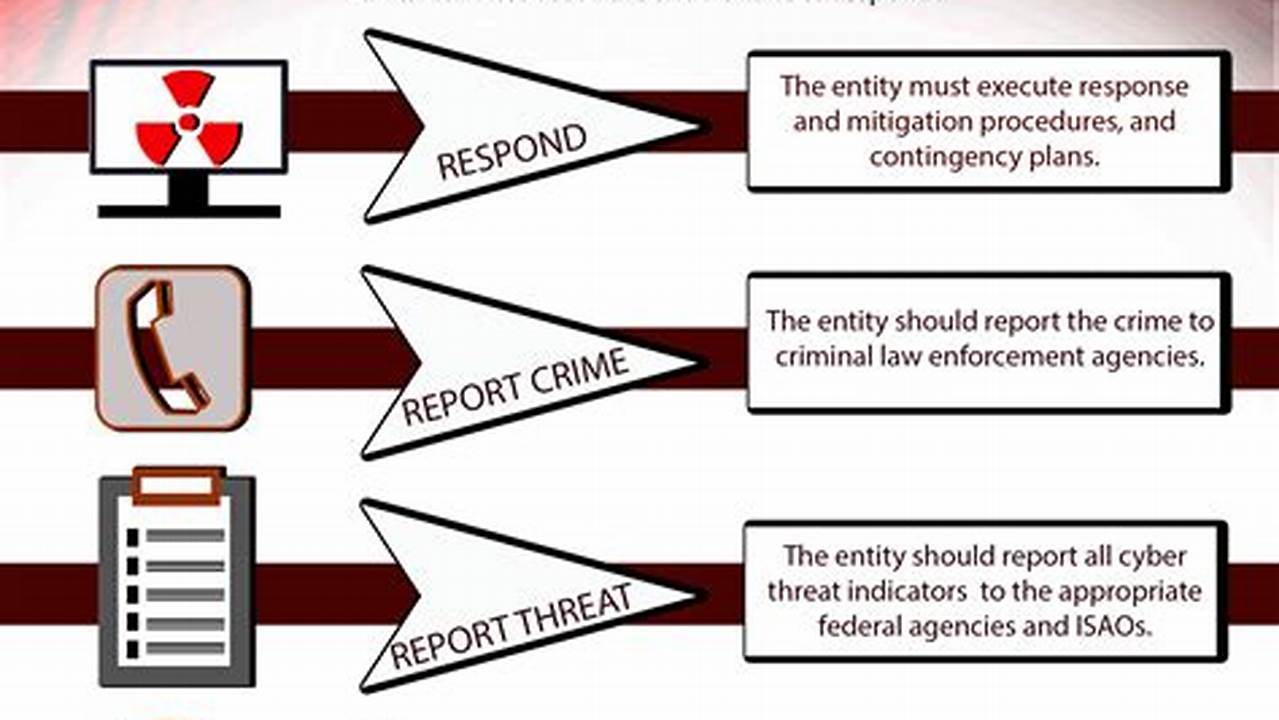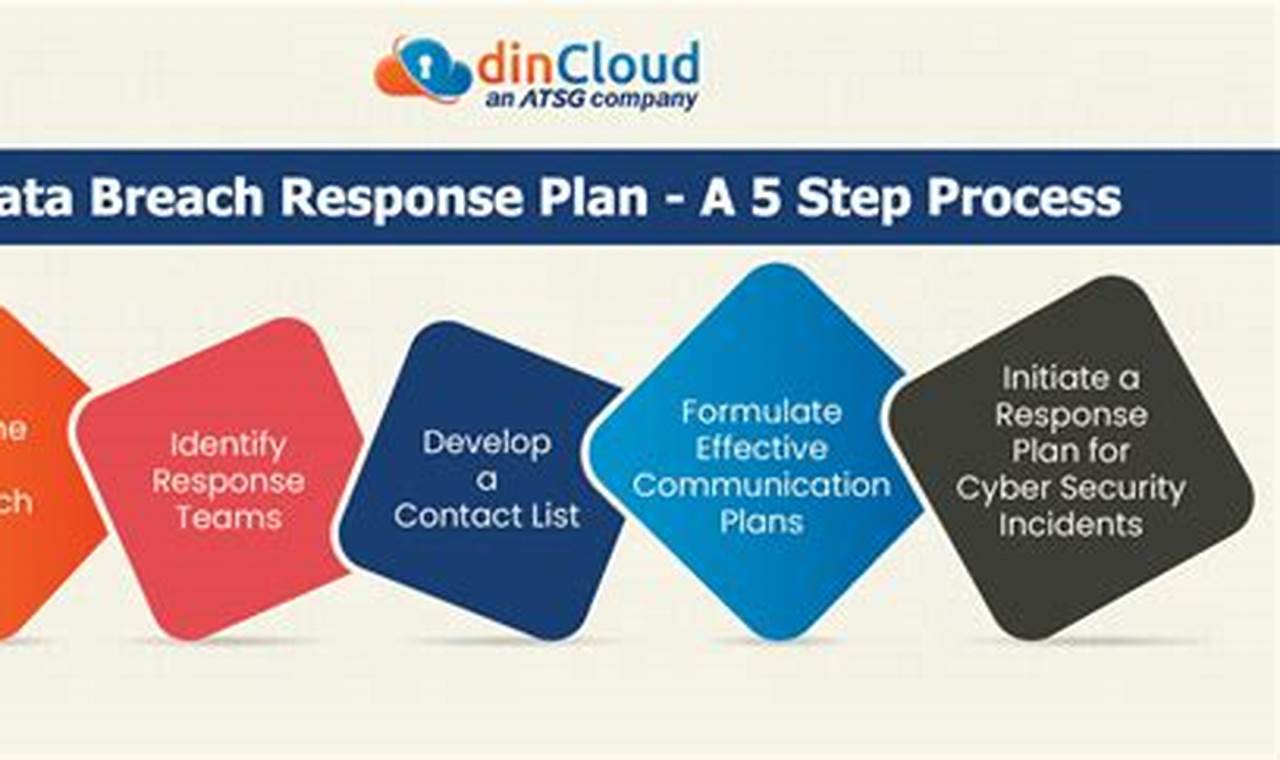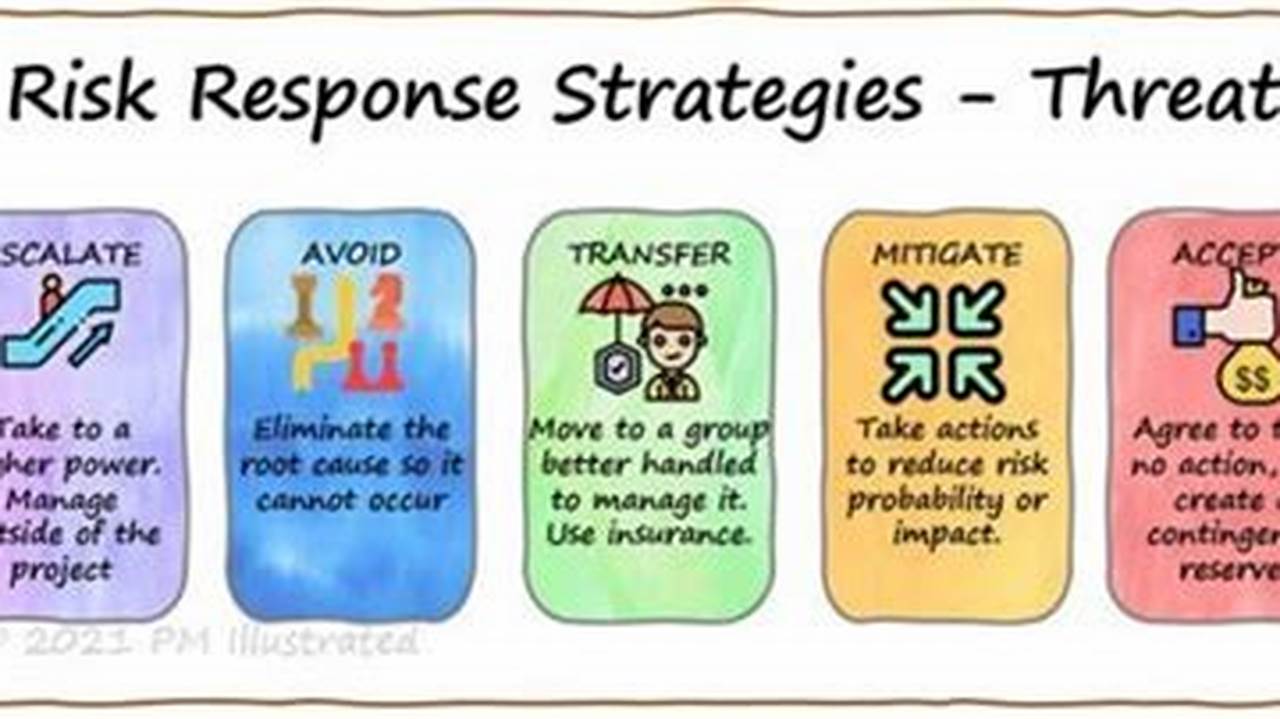
Every organization faces unique threats and challenges that can impact its operations, reputation, and financial stability. Threat response strategies are a set of proactive and reactive measures designed to identify, assess, and mitigate potential threats to an organization. These strategies are crucial for ensuring business continuity and minimizing the impact of security incidents, data breaches, natural disasters, or other disruptive events.
Effective threat response strategies involve a comprehensive approach that encompasses risk assessment, vulnerability management, incident response planning, and business continuity planning. By proactively identifying potential threats and implementing appropriate safeguards, organizations can reduce the likelihood of security breaches and minimize the impact of successful attacks. Threat response strategies also provide a framework for responding to incidents in a timely and coordinated manner, ensuring that the organization can quickly recover and resume normal operations.