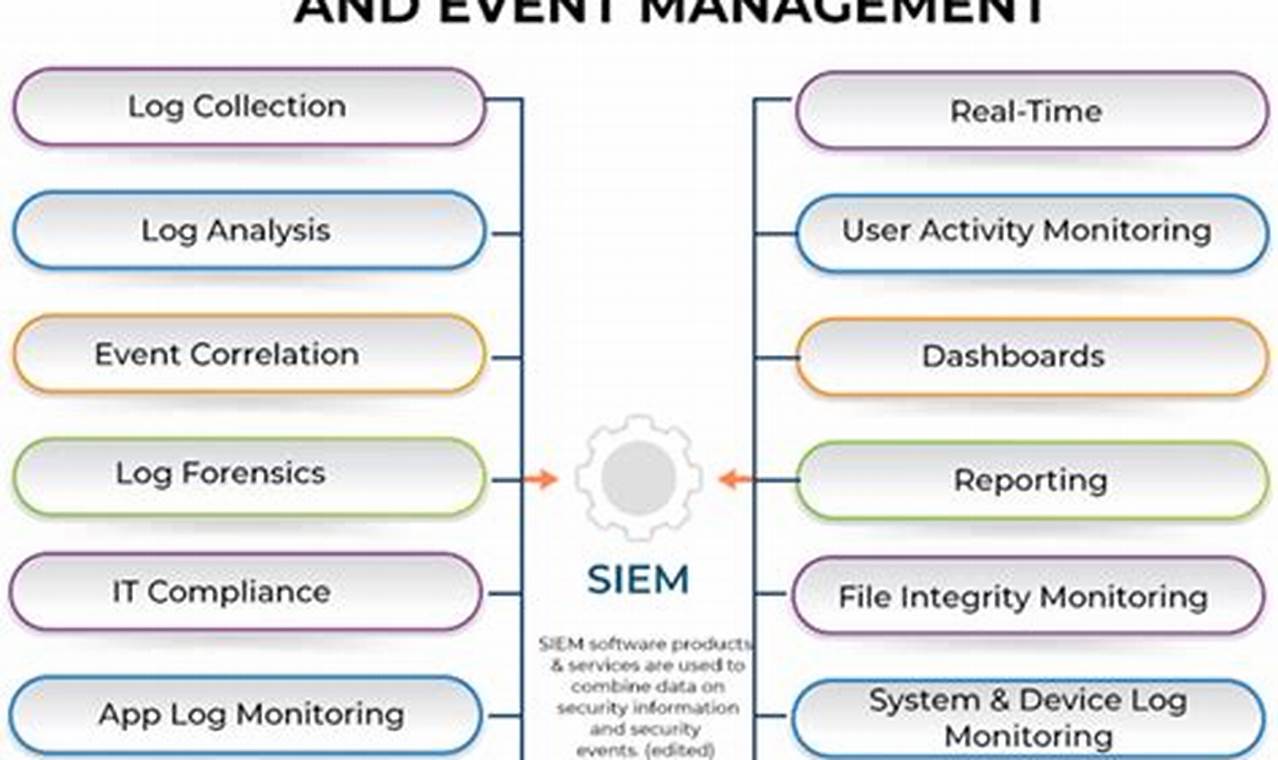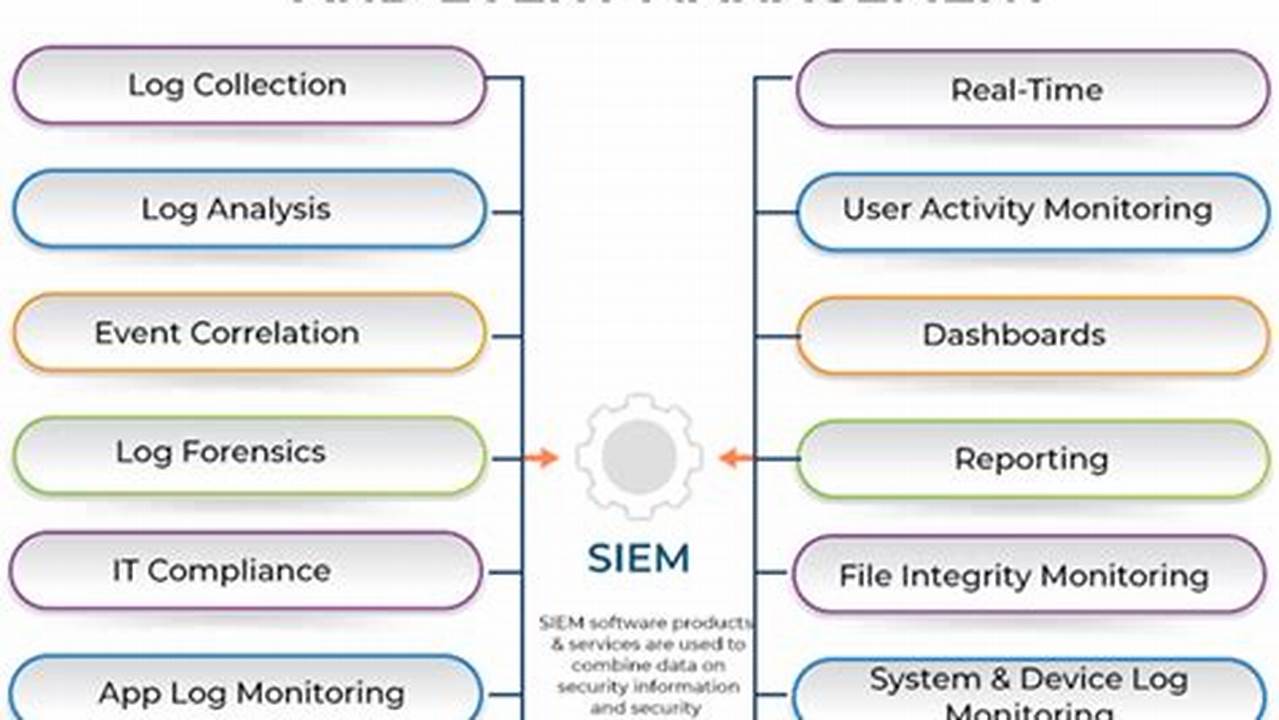
Security event management (SEM) is a process that involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats to an organization’s IT systems and data. This process helps organizations improve their security posture and reduce their risk of experiencing a security breach.
SEM is essential for organizations of all sizes, but it is particularly important for organizations that handle sensitive data or that are subject to regulatory compliance requirements. Organizations that fail to implement effective SEM processes are at increased risk of experiencing a security breach, which can result in financial losses, reputational damage, and legal liability.
The main article will discuss the following topics:
- The benefits of SEM
- The challenges of SEM
- The best practices for SEM
Security event management
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. Effective SEM can help organizations improve their security posture and reduce their risk of experiencing a security breach.
- Visibility: SEM provides organizations with visibility into their IT systems and data. This visibility enables organizations to identify and track security events, and to respond to threats in a timely manner.
- Detection: SEM can help organizations detect security events that may indicate a potential threat. These events may include unauthorized access to systems or data, or attempts to exploit vulnerabilities.
- Response: SEM can help organizations respond to security events in a timely and effective manner. This may involve isolating affected systems, blocking malicious traffic, or launching an investigation.
- Reporting: SEM can help organizations generate reports on security events. These reports can be used to identify trends, track progress, and meet regulatory compliance requirements.
- Compliance: SEM can help organizations meet regulatory compliance requirements. Many regulations require organizations to have a SEM process in place.
- Cost savings: SEM can help organizations save money by reducing the risk of a security breach. A security breach can result in financial losses, reputational damage, and legal liability.
In conclusion, SEM is a critical process for organizations of all sizes. SEM can help organizations improve their security posture, reduce their risk of experiencing a security breach, and meet regulatory compliance requirements.
Visibility: SEM provides organizations with visibility into their IT systems and data. This visibility enables organizations to identify and track security events, and to respond to threats in a timely manner.
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. One of the most important benefits of SEM is that it provides organizations with visibility into their IT systems and data.
- Improved threat detection: Visibility into IT systems and data enables organizations to identify and track security events that may indicate a potential threat. For example, SEM can be used to detect unauthorized access to systems or data, or attempts to exploit vulnerabilities.
- Faster response to threats: Visibility into IT systems and data enables organizations to respond to security events in a timely and effective manner. For example, SEM can be used to isolate affected systems, block malicious traffic, or launch an investigation.
- Improved compliance: Visibility into IT systems and data can help organizations meet regulatory compliance requirements. Many regulations require organizations to have a SEM process in place.
In conclusion, visibility is a critical component of SEM. SEM provides organizations with the visibility they need to identify and track security events, respond to threats in a timely manner, and meet regulatory compliance requirements.
Detection: SEM can help organizations detect security events that may indicate a potential threat. These events may include unauthorized access to systems or data, or attempts to exploit vulnerabilities.
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. One of the most important benefits of SEM is that it can help organizations detect security events that may indicate a potential threat.
- Early warning system: SEM can act as an early warning system for organizations, providing them with the information they need to identify and respond to potential threats before they can cause significant damage.
- Improved threat intelligence: SEM can help organizations improve their threat intelligence by providing them with data on security events that have occurred within their network. This data can be used to identify trends and patterns, and to develop more effective security strategies.
- Reduced risk of a security breach: SEM can help organizations reduce their risk of experiencing a security breach by detecting and mitigating potential threats before they can exploit vulnerabilities and compromise systems.
In conclusion, SEM is a critical tool for organizations looking to improve their security posture and reduce their risk of experiencing a security breach. SEM can help organizations detect security events that may indicate a potential threat, and provide them with the information they need to respond to threats in a timely and effective manner.
Response: SEM can help organizations respond to security events in a timely and effective manner. This may involve isolating affected systems, blocking malicious traffic, or launching an investigation.
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. One of the most important benefits of SEM is that it can help organizations respond to security events in a timely and effective manner.
When a security event occurs, SEM can provide organizations with the information they need to identify the affected systems, block malicious traffic, and launch an investigation. This can help organizations to minimize the damage caused by the security event and to prevent similar events from occurring in the future.
For example, if SEM detects that a server has been compromised, the organization can use SEM to identify the affected systems and isolate them from the network. This can prevent the malware from spreading to other systems and causing further damage.
SEM can also help organizations to block malicious traffic. For example, if SEM detects that a particular IP address is sending malicious traffic to the organization’s network, the organization can use SEM to block that IP address from accessing the network.
In addition, SEM can help organizations to launch investigations into security events. For example, if SEM detects that a user account has been compromised, the organization can use SEM to investigate the incident and determine how the account was compromised.
SEM is a critical tool for organizations looking to improve their security posture and reduce their risk of experiencing a security breach. SEM can help organizations to detect security events, respond to security events in a timely and effective manner, and investigate security events to prevent similar events from occurring in the future.
Reporting: SEM can help organizations generate reports on security events. These reports can be used to identify trends, track progress, and meet regulatory compliance requirements.
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. Reporting is an essential component of SEM, as it provides organizations with the visibility they need to identify trends, track progress, and meet regulatory compliance requirements.
Security event reports can be used to identify trends in security events. For example, an organization may notice an increase in the number of phishing attacks or ransomware attacks. This information can be used to develop more effective security strategies and to allocate resources more efficiently.
Security event reports can also be used to track progress in improving the organization’s security posture. For example, an organization may track the number of security events that are detected and mitigated each month. This information can be used to measure the effectiveness of the organization’s SEM program and to make necessary adjustments.
Finally, security event reports can be used to meet regulatory compliance requirements. Many regulations require organizations to have a SEM program in place and to generate regular security event reports.
In conclusion, reporting is an essential component of SEM. SEM provides organizations with the visibility they need to identify trends, track progress, and meet regulatory compliance requirements.
Compliance: SEM can help organizations meet regulatory compliance requirements. Many regulations require organizations to have a SEM process in place.
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. One of the many benefits of SEM is that it can help organizations meet regulatory compliance requirements.
- Improved visibility and control: SEM provides organizations with improved visibility into their IT systems and data. This visibility enables organizations to better understand their security risks and to take steps to mitigate those risks. This improved visibility and control can help organizations to meet regulatory compliance requirements that require organizations to have a clear understanding of their security risks and to have implemented appropriate security controls.
- Automated reporting: SEM solutions can generate automated reports on security events. These reports can be used to demonstrate compliance with regulatory requirements. For example, many regulations require organizations to report security breaches to regulatory authorities. SEM solutions can automate this process, making it easier for organizations to comply with these requirements.
- Reduced risk of fines and penalties: Organizations that fail to comply with regulatory requirements can face fines and penalties. SEM can help organizations to reduce their risk of fines and penalties by providing them with the visibility and control they need to meet regulatory compliance requirements.
In conclusion, SEM is a critical tool for organizations that need to meet regulatory compliance requirements. SEM can provide organizations with improved visibility into their IT systems and data, automated reporting, and reduced risk of fines and penalties.
Cost savings: SEM can help organizations save money by reducing the risk of a security breach. A security breach can result in financial losses, reputational damage, and legal liability.
Security event management (SEM) is a critical process for organizations of all sizes. SEM can help organizations identify and mitigate potential threats to their IT systems and data. By reducing the risk of a security breach, SEM can help organizations save money in a number of ways.
- Reduced financial losses: A security breach can result in significant financial losses for organizations. These losses can include the cost of repairing damaged systems, recovering lost data, and compensating victims of the breach. SEM can help organizations to reduce their financial losses by identifying and mitigating potential threats before they can cause damage.
- Reduced reputational damage: A security breach can also damage an organization’s reputation. This damage can lead to lost customers, partners, and investors. SEM can help organizations to protect their reputation by identifying and mitigating potential threats before they can cause damage.
- Reduced legal liability: A security breach can also result in legal liability for organizations. This liability can include fines, penalties, and lawsuits. SEM can help organizations to reduce their legal liability by identifying and mitigating potential threats before they can cause damage.
In conclusion, SEM is a critical tool for organizations that want to save money. SEM can help organizations to reduce their financial losses, protect their reputation, and reduce their legal liability.
Security Event Management FAQs
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. Here are some frequently asked questions about SEM:
Question 1: What are the benefits of SEM?
SEM provides a number of benefits for organizations, including improved visibility into IT systems and data, faster detection and response to security threats, and reduced risk of security breaches.
Question 2: What are the challenges of SEM?
SEM can be challenging to implement and manage, especially for organizations with large and complex IT environments. Challenges include collecting and analyzing large volumes of data, identifying and prioritizing security threats, and responding to security events in a timely and effective manner.
Question 3: What are the best practices for SEM?
There are a number of best practices for SEM, including using a SIEM (security information and event management) solution, implementing a security monitoring plan, and training staff on SEM procedures.
Question 4: What are the common mistakes to avoid in SEM?
There are a number of common mistakes to avoid in SEM, including failing to collect and analyze sufficient data, failing to identify and prioritize security threats, and failing to respond to security events in a timely and effective manner.
Question 5: What are the trends in SEM?
There are a number of trends in SEM, including the increasing use of AI and machine learning to detect and respond to security threats, the adoption of cloud-based SIEM solutions, and the growing focus on compliance and regulatory requirements.
Question 6: What are the resources available for learning more about SEM?
There are a number of resources available for learning more about SEM, including books, articles, white papers, and training courses.
SEM is a critical tool for organizations looking to improve their security posture and reduce their risk of experiencing a security breach. By understanding the benefits, challenges, and best practices of SEM, organizations can implement an effective SEM program that meets their specific needs.
Next Article Section: Security Event Management Best Practices
Security Event Management Tips
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. Here are five tips for effective SEM:
Tip 1: Use a SIEM solution
A SIEM (security information and event management) solution can help you to collect, store, and analyze security events from a variety of sources. This can give you a comprehensive view of your security environment and help you to identify threats more quickly.
Tip 2: Implement a security monitoring plan
A security monitoring plan will help you to define the specific security events that you want to monitor, and the actions that you will take when those events occur. This will help you to respond to security threats in a timely and effective manner.
Tip 3: Train staff on SEM procedures
Your staff need to be trained on SEM procedures so that they know how to respond to security events. This training should include how to identify security events, how to prioritize security events, and how to respond to security events.
Tip 4: Test your SEM program
It is important to test your SEM program on a regular basis to ensure that it is working properly. This testing should include simulating security events and testing your response procedures.
Tip 5: Keep your SEM program up to date
The threat landscape is constantly changing, so it is important to keep your SEM program up to date. This includes updating your SIEM solution, your security monitoring plan, and your staff training.By following these tips, you can improve the effectiveness of your SEM program and reduce your risk of experiencing a security breach.
Next Article Section: Security Event Management Best Practices
Conclusion
Security event management (SEM) is a critical process for organizations of all sizes. SEM involves collecting, monitoring, and analyzing security events to identify and mitigate potential threats. SEM can help organizations to improve their security posture, reduce their risk of experiencing a security breach, and meet regulatory compliance requirements.
Organizations should implement a comprehensive SEM program that includes the use of a SIEM solution, a security monitoring plan, and trained staff. By following these best practices, organizations can improve the effectiveness of their SEM program and protect their critical assets from cyber threats.
Youtube Video: