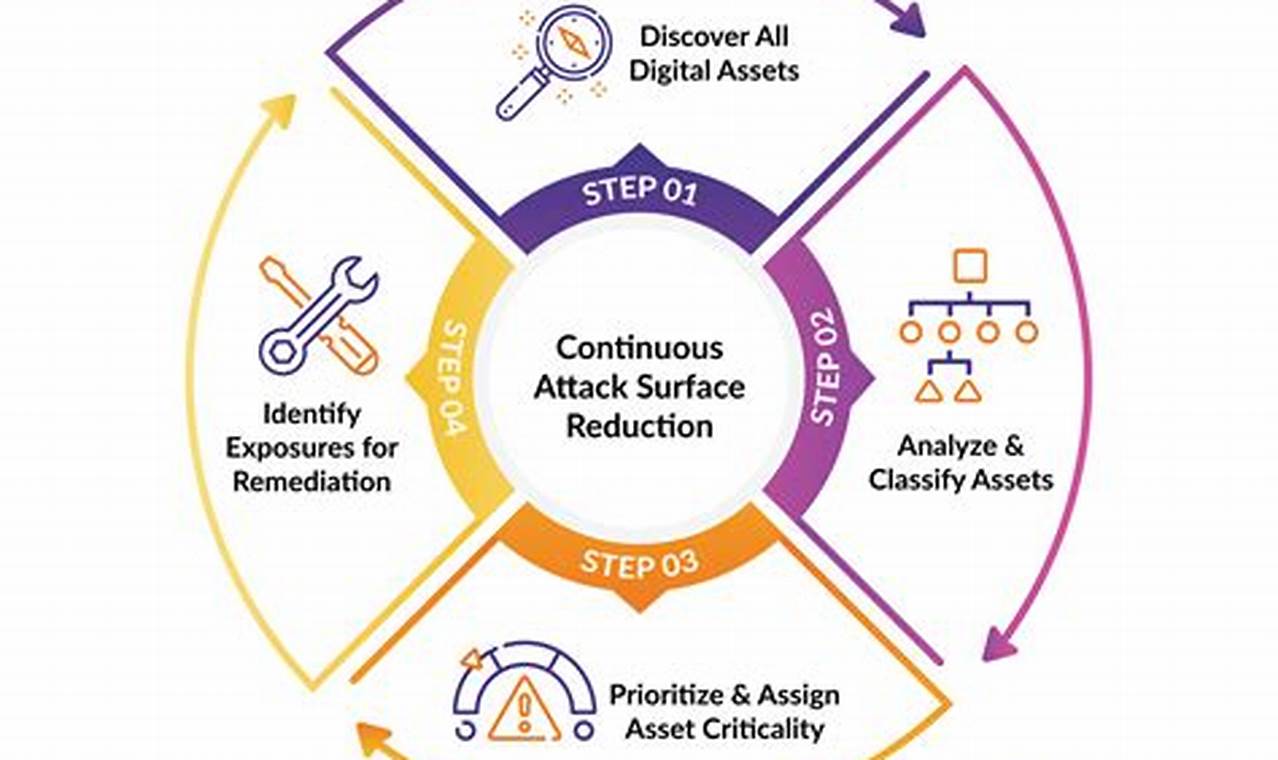
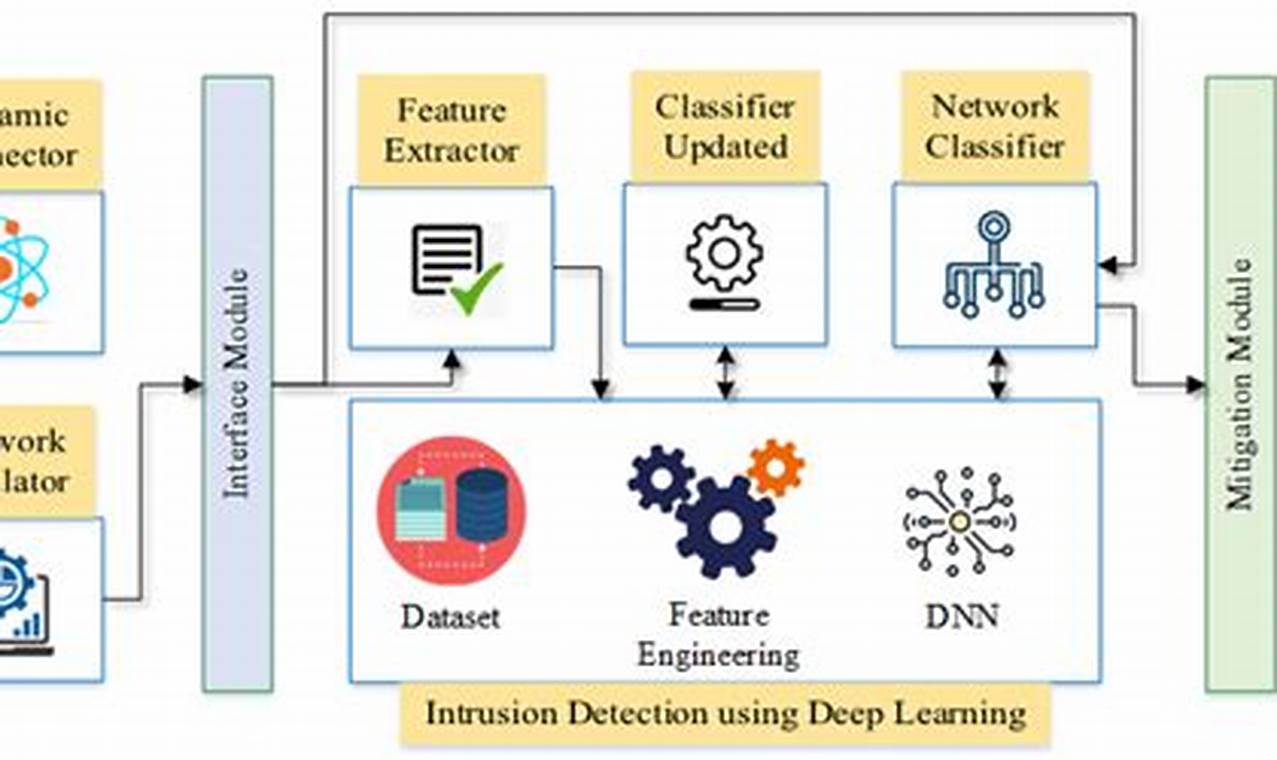
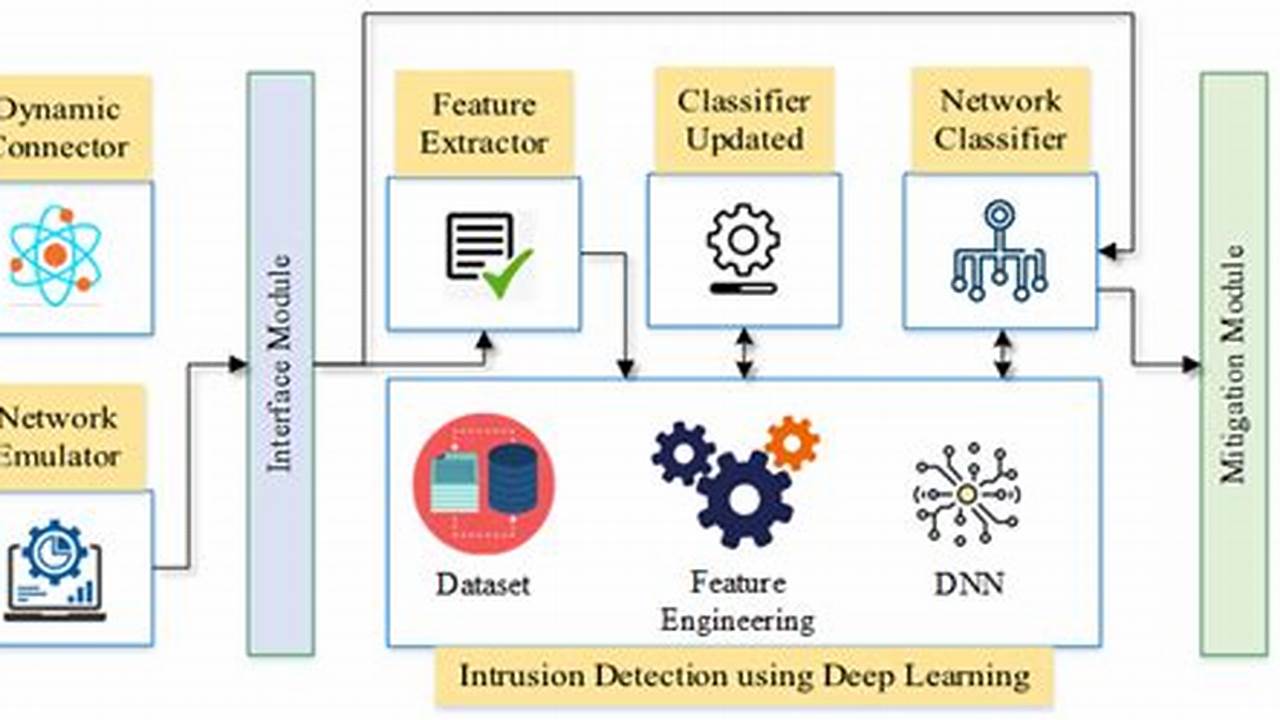
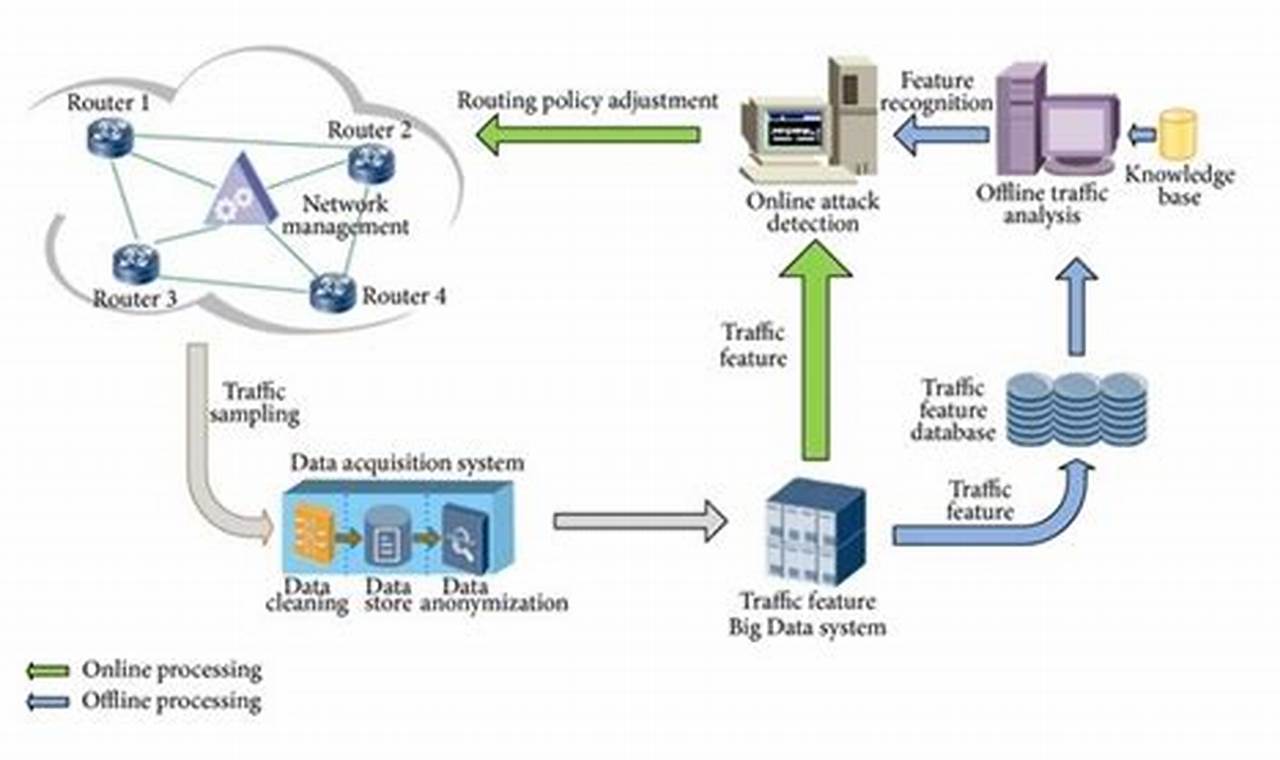
Attack surface reduction refers to the intentional reduction of the number of potential entry points that an attacker can use to access a computer system or network. This is typically achieved through a combination of security measures, such as patching software, implementing firewalls, and using intrusion detection systems. By reducing the attack surface, organizations can make it more difficult for attackers to gain access to their systems and data.
Attack surface reduction is an important part of any comprehensive cybersecurity strategy. By reducing the number of potential entry points for attackers, organizations can make it more difficult for them to compromise their systems. This can help to protect sensitive data, prevent financial losses, and maintain the reputation of the organization.