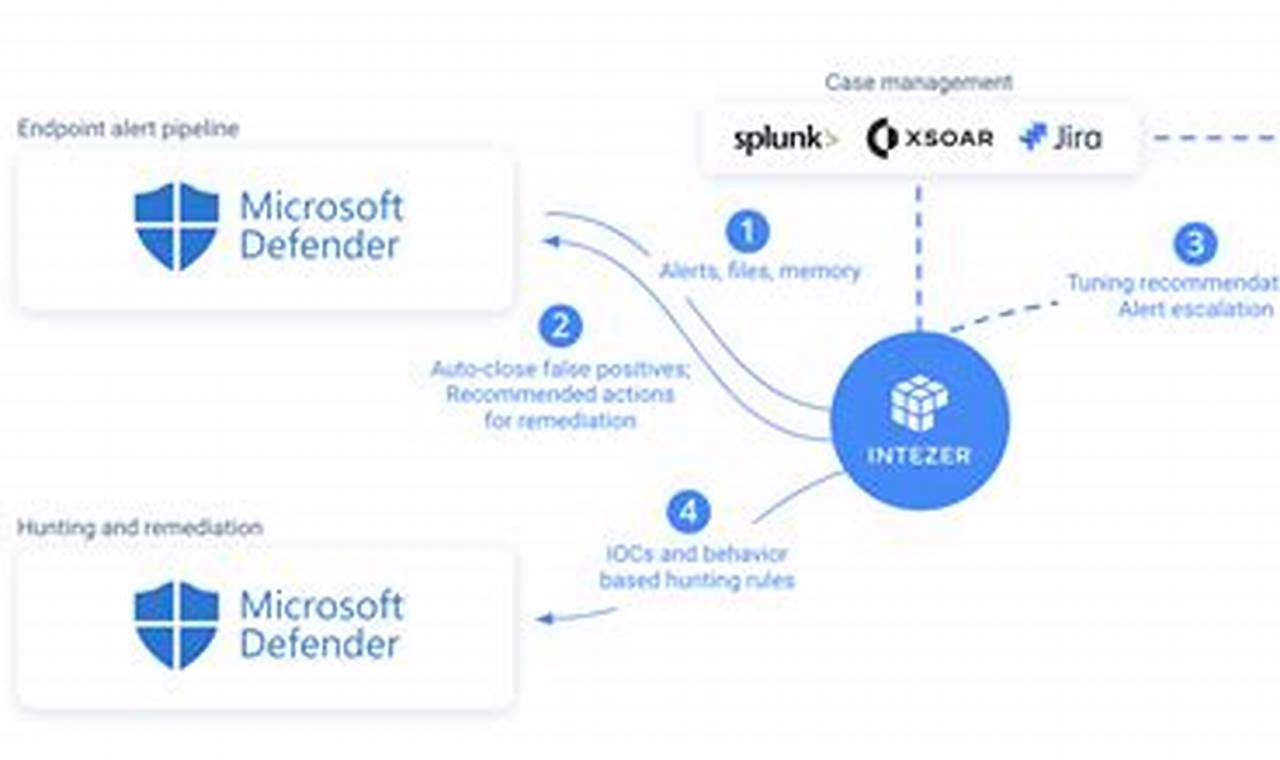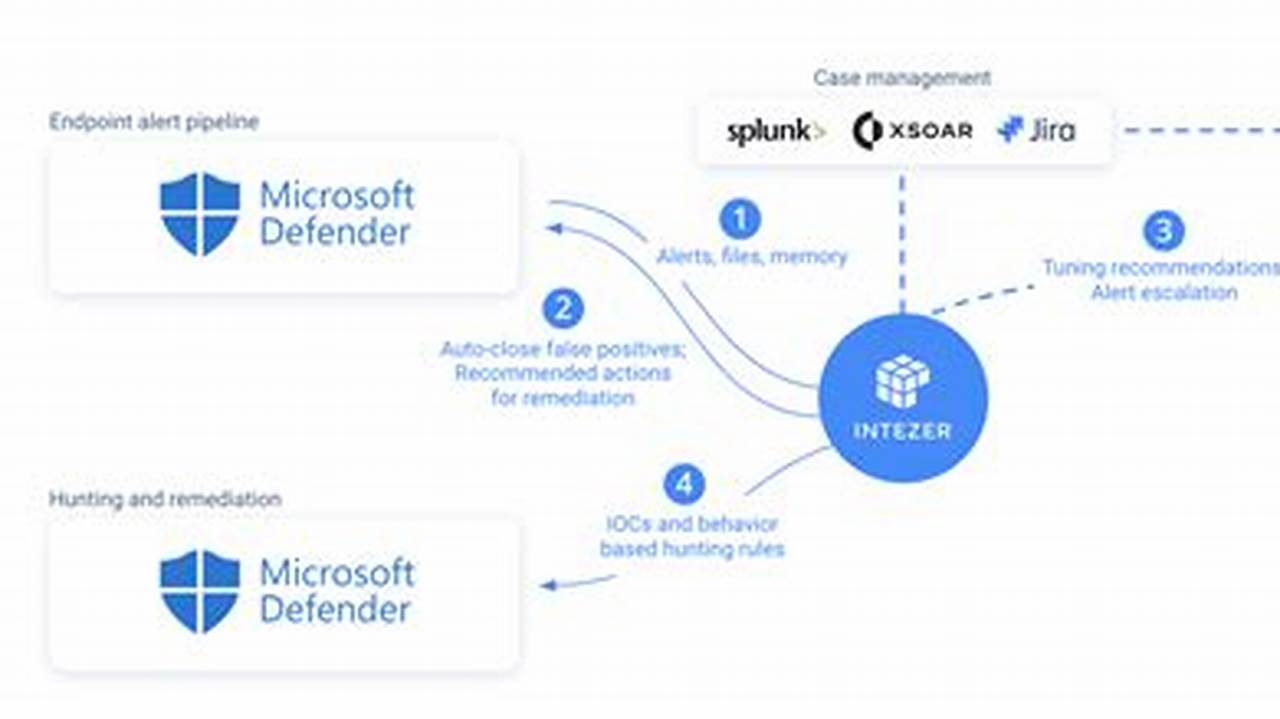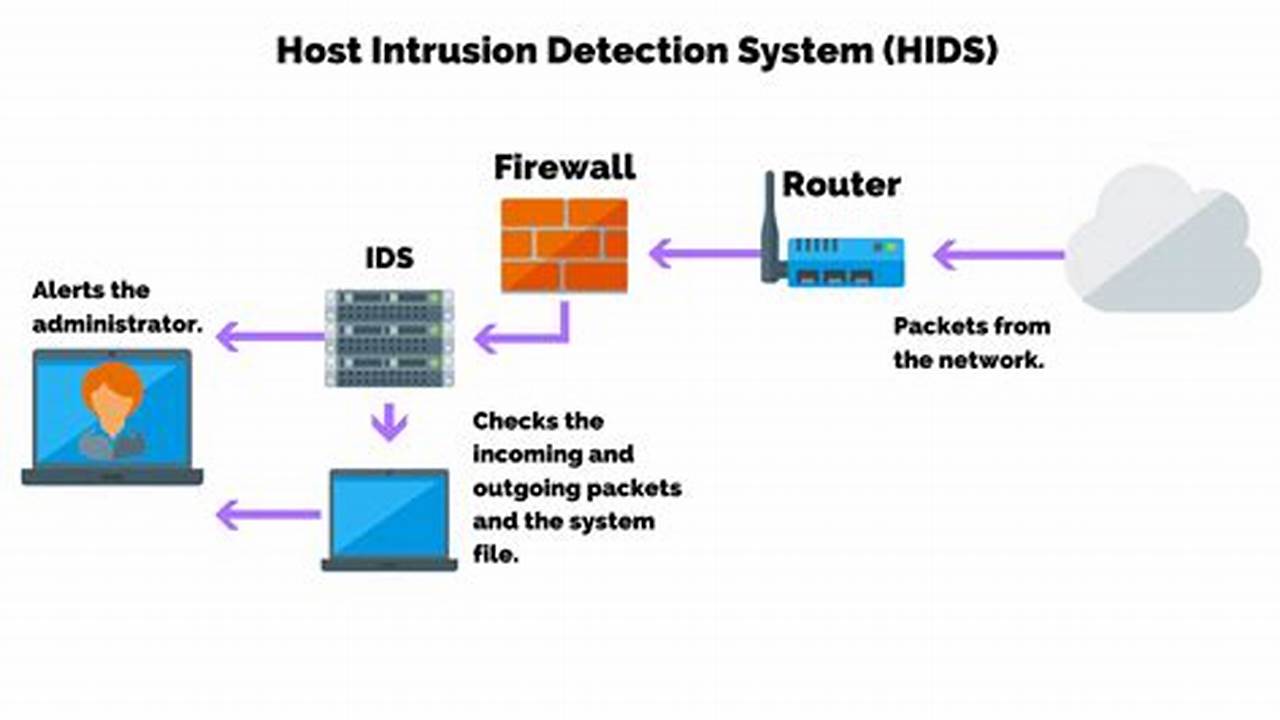
Host intrusion detection systems (HIDSs) monitor a host computer or network for suspicious activity. They can detect a variety of attacks, including unauthorized access, file modifications, and privilege escalation. HIDSs use a variety of techniques to detect attacks, including file integrity monitoring, process monitoring, and network traffic analysis.
HIDSs are an important part of a comprehensive security strategy. They can help to protect against a wide range of attacks and can provide early warning of security breaches. HIDSs have been used for many years and have a proven track record of success.