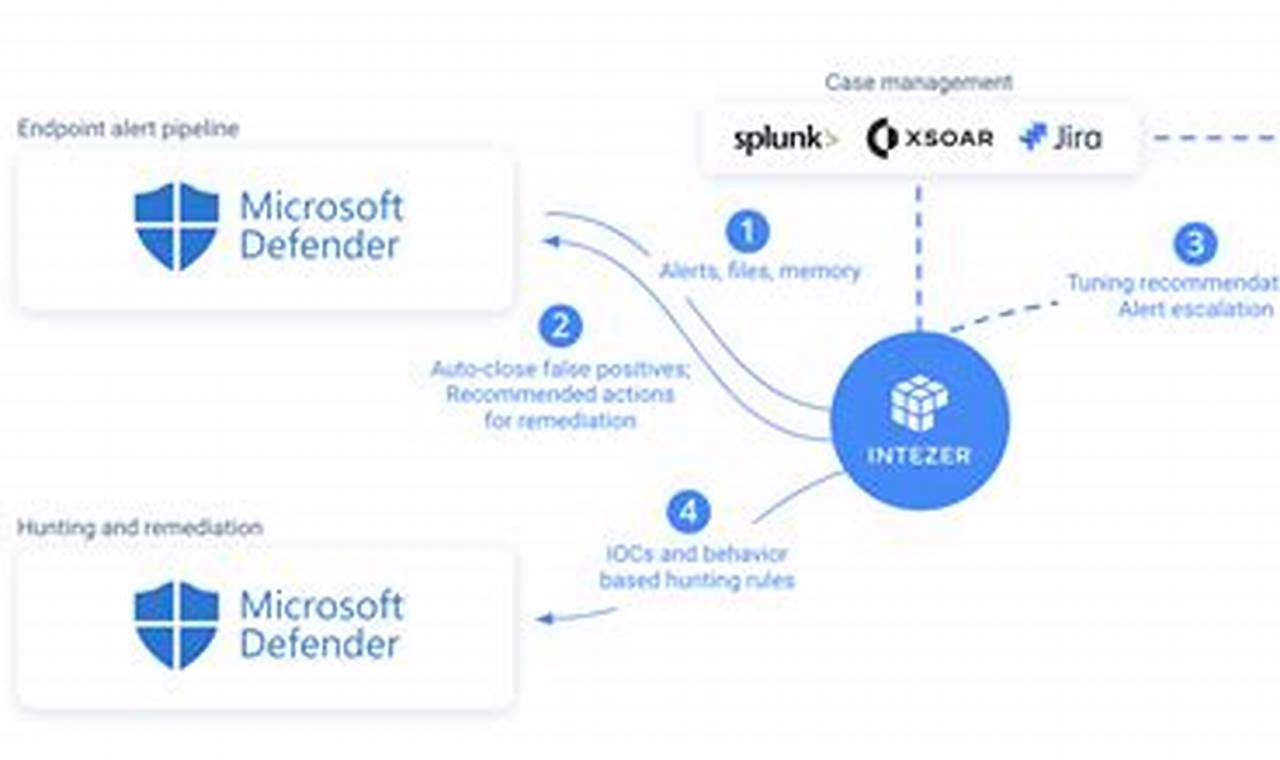
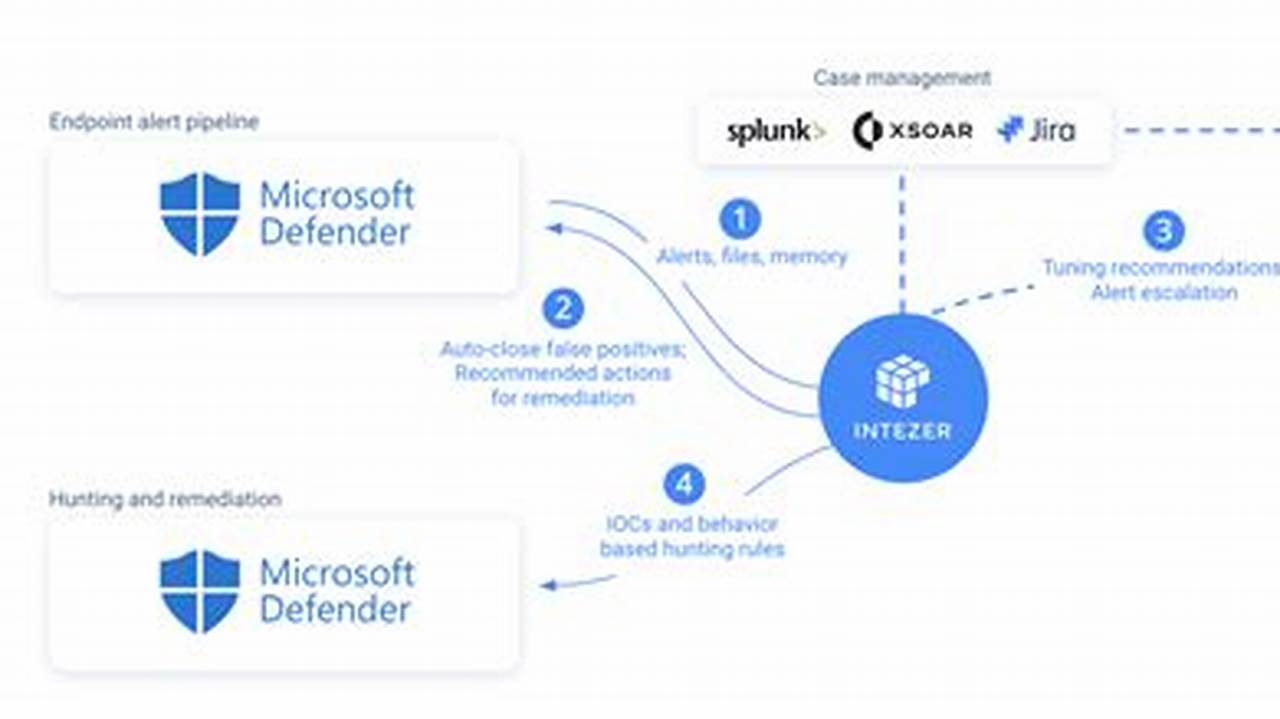
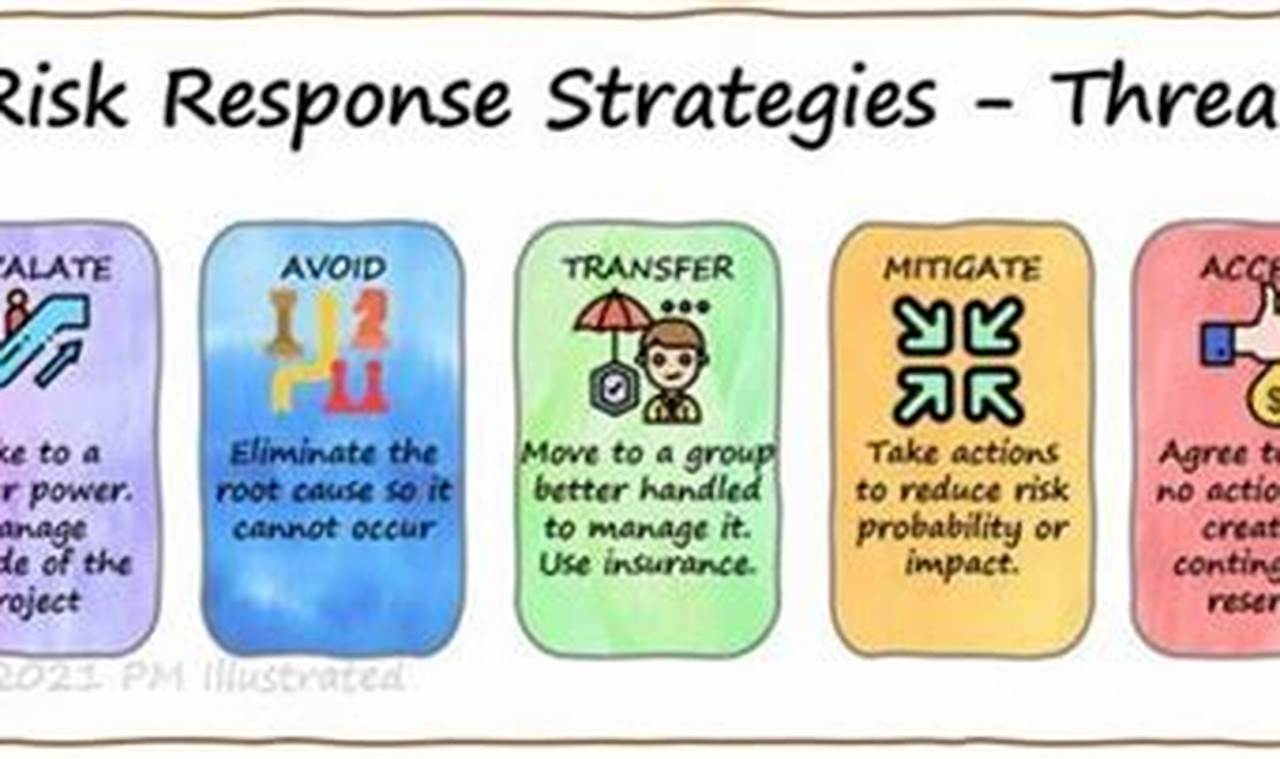
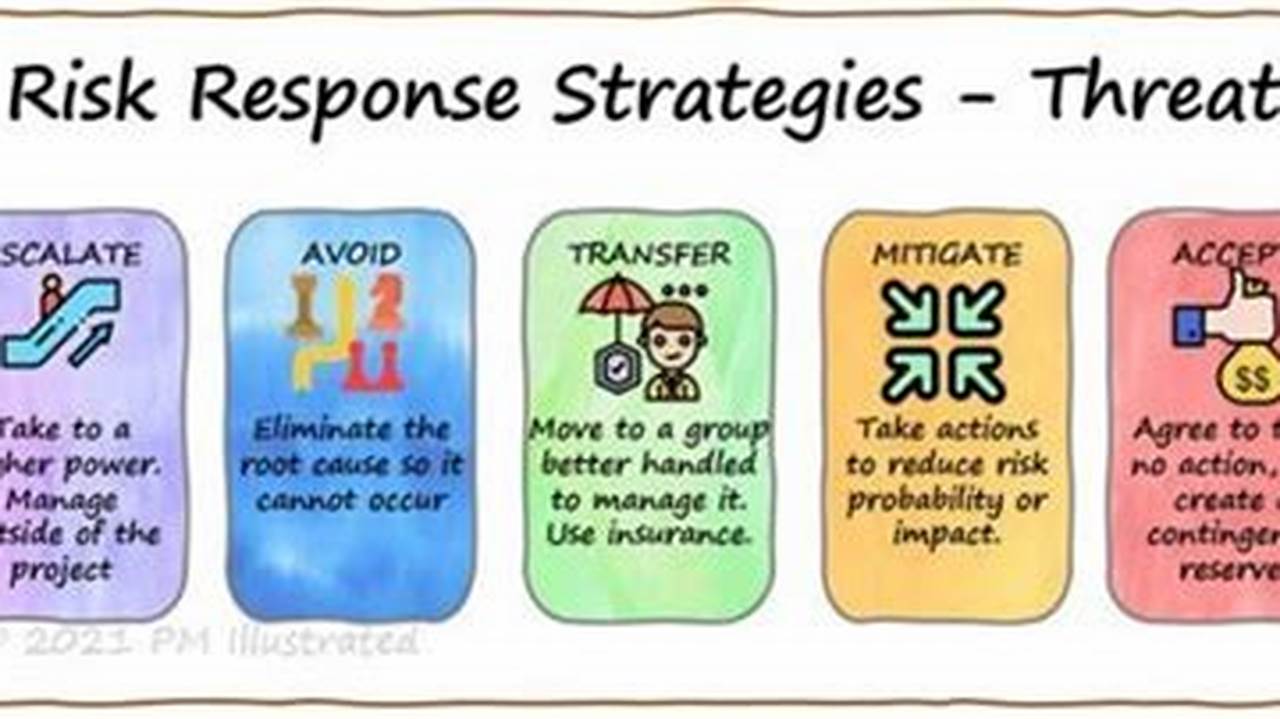
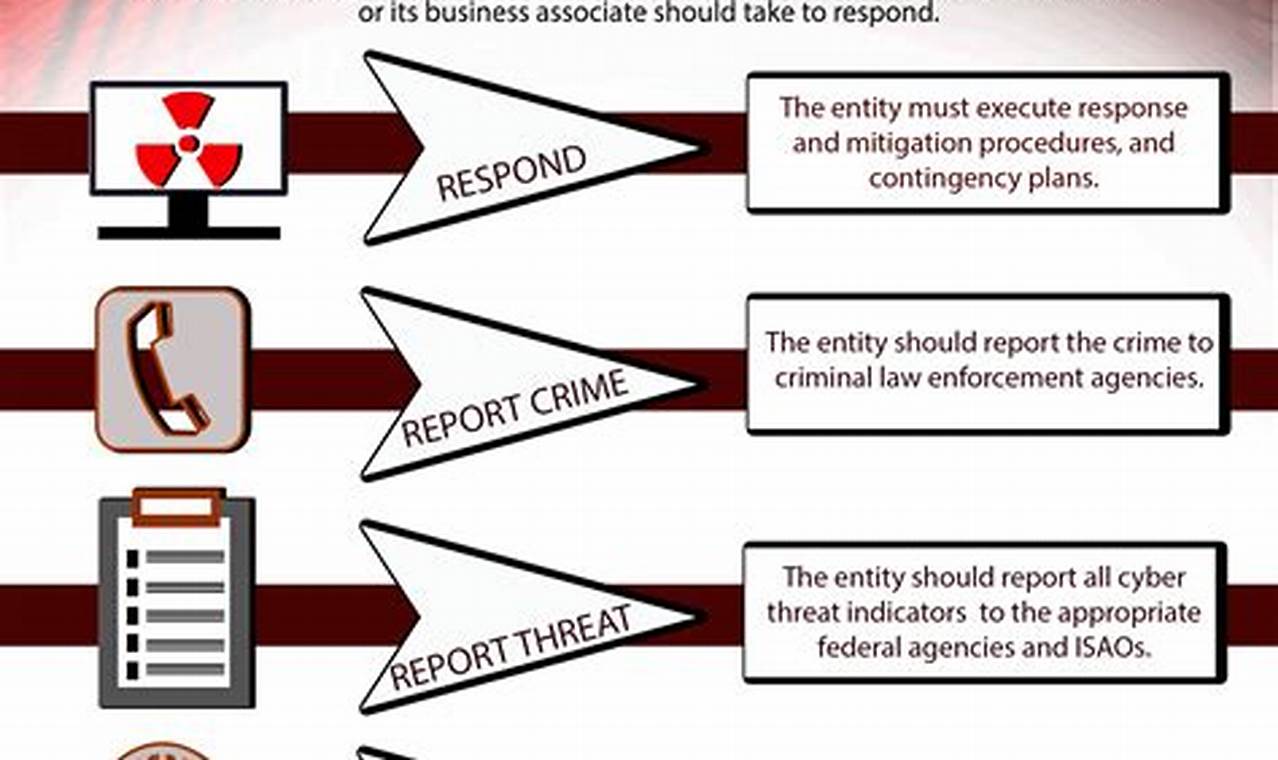
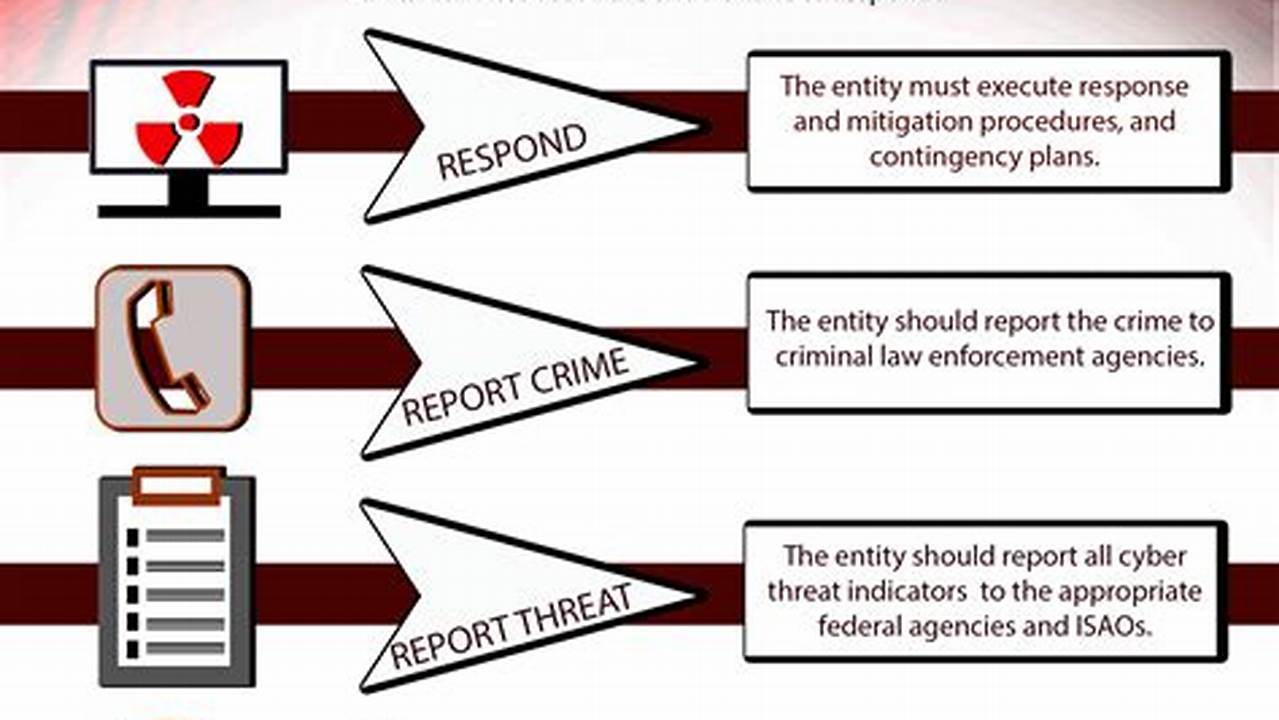
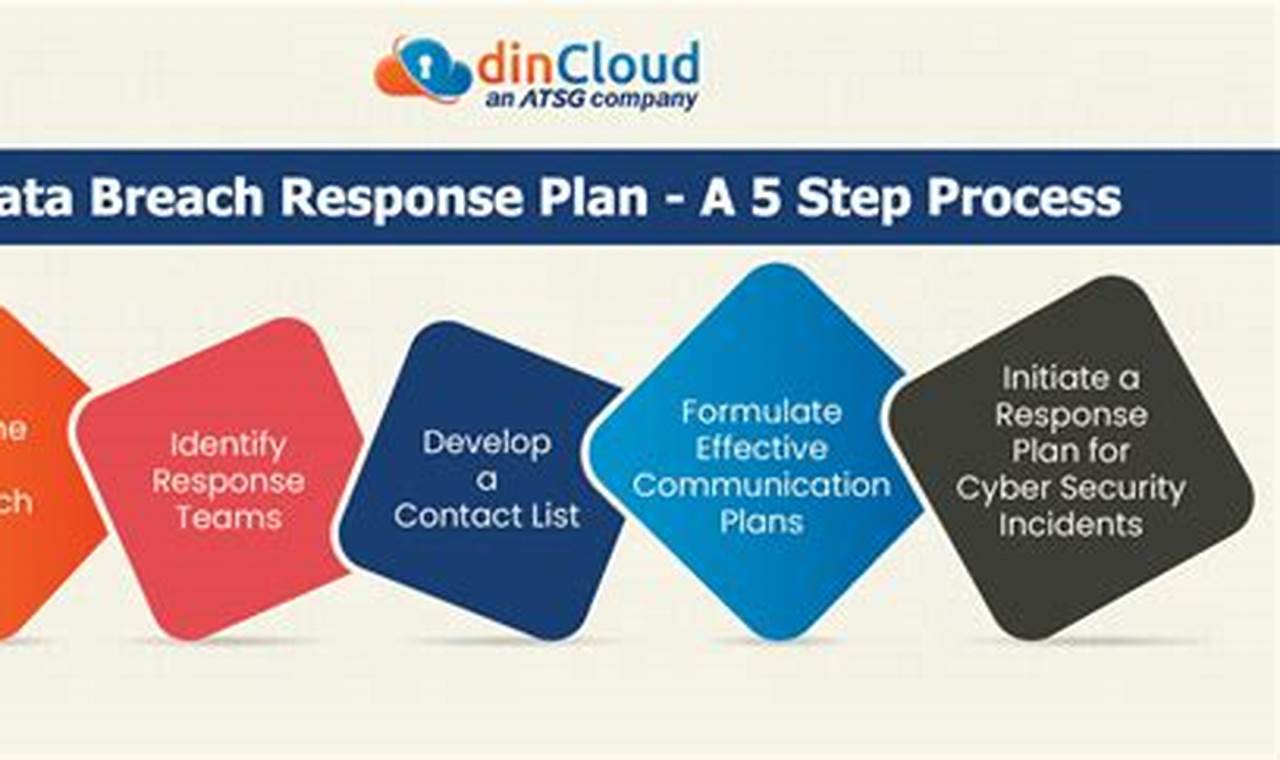
Threat detection and response is the process of identifying and mitigating cybersecurity threats. It involves monitoring and analyzing network traffic, endpoint activity, and user behavior for suspicious activity. When a threat is detected, the response team takes action to contain and neutralize the threat, such as isolating infected systems, patching vulnerabilities, or implementing additional security measures.
Threat detection and response is a critical component of any cybersecurity strategy. It helps organizations to protect their data, systems, and reputation from cyberattacks. By quickly detecting and responding to threats, organizations can minimize the impact of an attack and reduce the risk of future attacks.