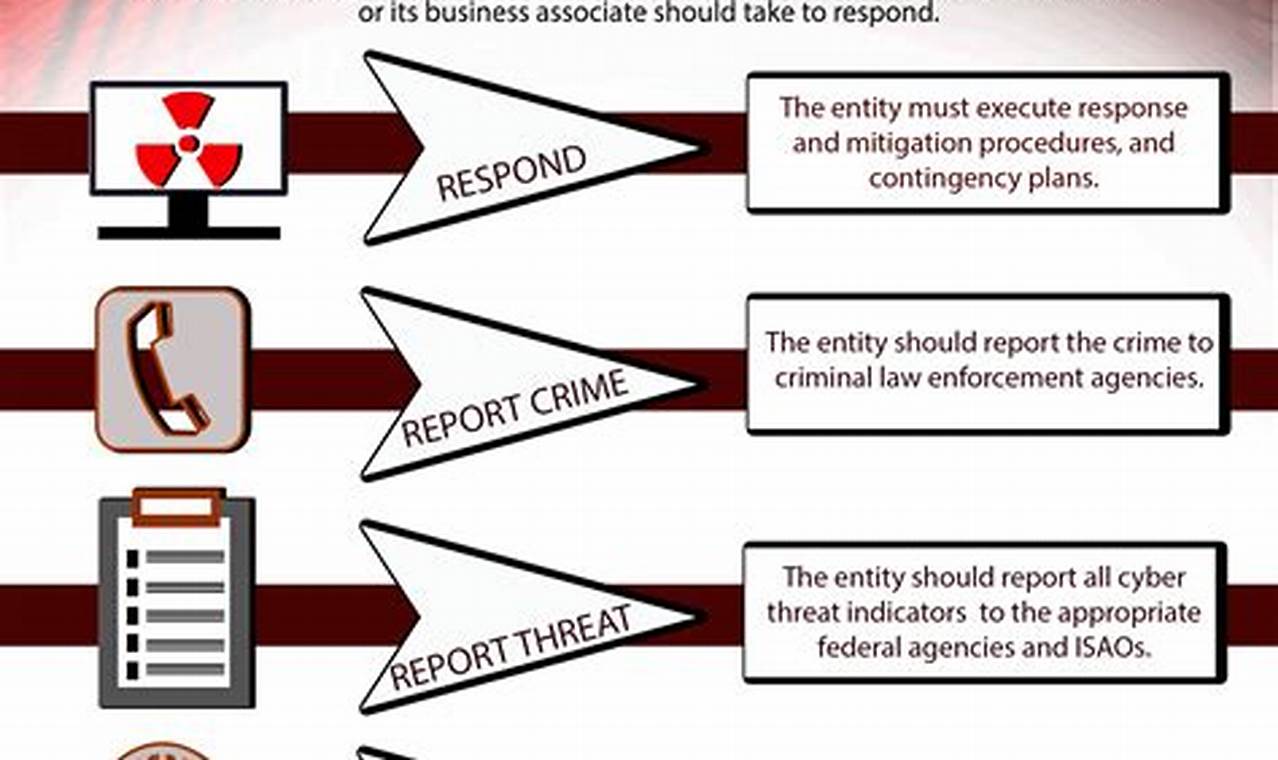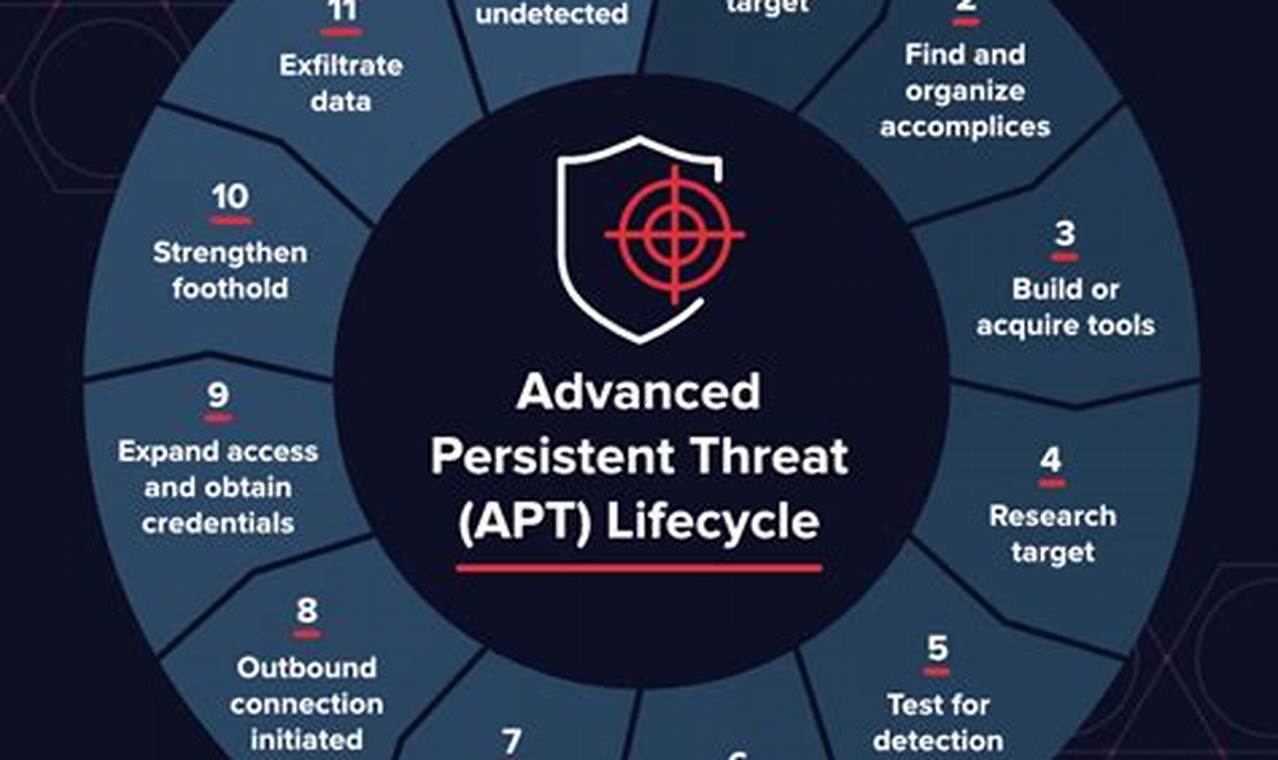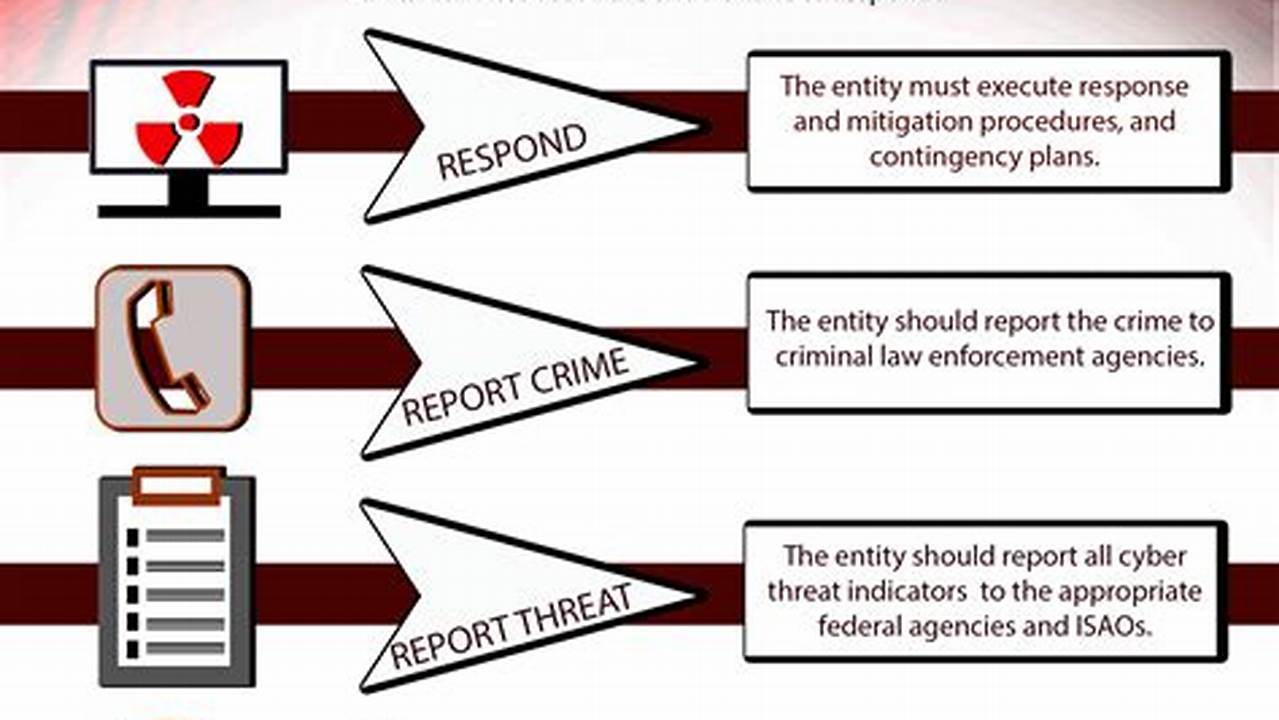
Cyber threat response encompasses the processes and procedures designed to identify, analyze, and mitigate cyber threats. These threats can manifest in various forms, such as malware attacks, phishing scams, or unauthorized access attempts to networks and systems.
Implementing a robust cyber threat response plan is crucial for organizations to protect their sensitive data, maintain operational efficiency, and uphold customer trust. By swiftly identifying and responding to cyber threats, organizations can minimize potential damage, reduce downtime, and maintain business continuity.