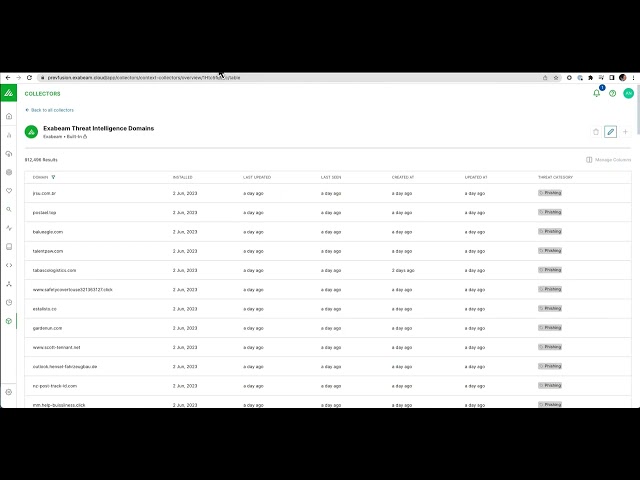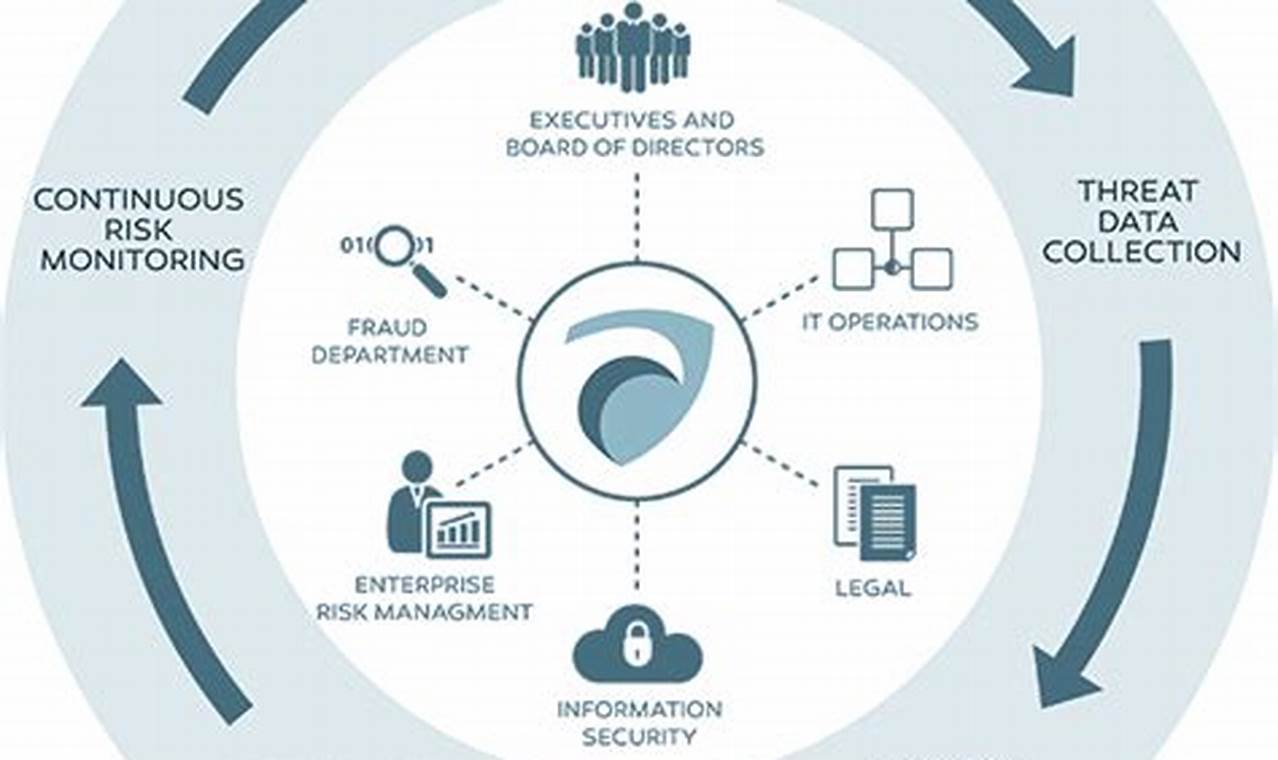
Threat intelligence integration is the process of collecting, analyzing, and sharing information about threats to an organization’s assets. This information can come from a variety of sources, including internal security logs, external threat intelligence feeds, and open-source reports. Threat intelligence integration is crucial to identify vulnerabilities, detect threats, and respond to incidents in a timely and effective manner.
There are many benefits to threat intelligence integration, including:
- Improved situational awareness: Threat intelligence integration can give organizations a better understanding of the threats they face and the likelihood of these threats occurring.
- Faster response times: Threat intelligence integration can help organizations to detect and respond to threats more quickly, reducing the impact of these threats.
- Improved security posture: Threat intelligence integration can help organizations to improve their overall security posture by identifying and mitigating vulnerabilities.
Threat intelligence integration is a vital part of any organization’s security strategy. By collecting, analyzing, and sharing information about threats, organizations can better protect themselves from these threats and reduce the impact of any incidents that do occur.
Now that we have a better understanding of threat intelligence integration, we can move on to the main topics of this article.
Threat intelligence integration
Threat intelligence integration is a critical aspect of cybersecurity. It involves the collection, analysis, and sharing of information about threats to an organization’s assets. This information can come from a variety of sources, including internal security logs, external threat intelligence feeds, and open-source reports. Threat intelligence integration is essential for organizations to identify vulnerabilities, detect threats, and respond to incidents in a timely and effective manner.
- Collection: Gathering threat intelligence from various sources.
- Analysis: Making sense of the collected threat intelligence.
- Sharing: Distributing threat intelligence to relevant stakeholders.
- Integration: Incorporating threat intelligence into security systems and processes.
- Detection: Identifying threats based on integrated threat intelligence.
- Response: Taking appropriate actions to mitigate threats.
- Prevention: Using threat intelligence to prevent future threats.
These key aspects of threat intelligence integration are interconnected and essential for organizations to maintain a strong security posture. For example, organizations need to collect threat intelligence in order to analyze it and share it with relevant stakeholders. They also need to integrate threat intelligence into their security systems and processes in order to detect and respond to threats effectively. Finally, organizations need to use threat intelligence to prevent future threats by identifying and mitigating vulnerabilities in their systems and processes.
Collection
The collection of threat intelligence from various sources is the foundation of threat intelligence integration. This process involves gathering information about threats from a wide range of sources, including internal security logs, external threat intelligence feeds, and open-source reports. This information can then be analyzed and shared with relevant stakeholders to help organizations identify vulnerabilities, detect threats, and respond to incidents in a timely and effective manner.
- Internal security logs can provide valuable insights into the threats that an organization is facing. These logs can contain information about security events, such as failed login attempts, malware infections, and network intrusions. Analyzing these logs can help organizations to identify patterns and trends in threat activity, and to develop strategies to mitigate these threats.
- External threat intelligence feeds can provide organizations with access to information about threats that are targeting other organizations in their industry or sector. These feeds can be provided by commercial vendors or by government agencies, and they can contain information about new vulnerabilities, malware campaigns, and other threats. Organizations can use this information to stay ahead of the latest threats and to develop measures.
- Open-source reports can also be a valuable source of threat intelligence. These reports are often published by security researchers and analysts, and they can contain information about new vulnerabilities, malware campaigns, and other threats. Organizations can use this information to supplement their other threat intelligence sources and to gain a more comprehensive view of the threat landscape.
Collecting threat intelligence from various sources is essential for organizations to maintain a strong security posture. By gathering information about threats from a wide range of sources, organizations can better identify vulnerabilities, detect threats, and respond to incidents in a timely and effective manner.
Analysis
The analysis of collected threat intelligence is a critical step in the threat intelligence integration process. This process involves making sense of the collected threat intelligence and identifying patterns and trends in threat activity. This information can then be used to identify vulnerabilities, detect threats, and respond to incidents in a timely and effective manner.
- Identifying patterns and trends: Analyzing threat intelligence can help organizations to identify patterns and trends in threat activity. This information can be used to develop strategies to mitigate these threats and to prevent them from causing damage to the organization.
- Enhancing situational awareness: Analyzing threat intelligence can help organizations to enhance their situational awareness. This information can help organizations to understand the threats that they are facing and to make informed decisions about how to protect their assets.
- Identifying vulnerabilities: Analyzing threat intelligence can help organizations to identify vulnerabilities in their systems and processes. This information can be used to develop strategies to mitigate these vulnerabilities and to prevent them from being exploited by attackers.
- Developing threat models: Analyzing threat intelligence can help organizations to develop threat models. These models can be used to simulate different threat scenarios and to develop strategies to mitigate these threats.
The analysis of collected threat intelligence is essential for organizations to maintain a strong security posture. By making sense of the collected threat intelligence, organizations can better identify vulnerabilities, detect threats, and respond to incidents in a timely and effective manner.
Sharing
Sharing threat intelligence is a critical aspect of threat intelligence integration. It involves distributing threat intelligence to relevant stakeholders within an organization, such as security analysts, incident responders, and IT staff. Sharing threat intelligence helps to ensure that everyone in the organization has the information they need to identify, detect, and respond to threats in a timely and effective manner.
- Improved situational awareness: Sharing threat intelligence can help to improve the situational awareness of all stakeholders within an organization. By having access to the same information, stakeholders can better understand the threats that the organization is facing and make more informed decisions about how to protect the organization’s assets.
- Faster response times: Sharing threat intelligence can help to reduce response times to threats. By having access to the same information, stakeholders can quickly identify and respond to threats, reducing the impact of these threats.
- Improved collaboration: Sharing threat intelligence can help to improve collaboration between different stakeholders within an organization. By having access to the same information, stakeholders can work together more effectively to identify, detect, and respond to threats.
- Enhanced security posture: Sharing threat intelligence can help to enhance an organization’s overall security posture. By having access to the same information, stakeholders can better identify and mitigate vulnerabilities, reducing the risk of these vulnerabilities being exploited by attackers.
Sharing threat intelligence is essential for organizations to maintain a strong security posture. By distributing threat intelligence to relevant stakeholders, organizations can improve their situational awareness, reduce response times to threats, improve collaboration between different stakeholders, and enhance their overall security posture.
Integration
Integration is a critical aspect of threat intelligence integration. It involves incorporating threat intelligence into security systems and processes in order to identify, detect, and respond to threats in a timely and effective manner.
- Automated threat detection: Threat intelligence can be integrated into security systems to automate the detection of threats. This can be done by using threat intelligence feeds to identify malicious IP addresses, URLs, and file hashes. When a security system detects a threat, it can automatically take action, such as blocking the threat or quarantining the infected system.
- Improved incident response: Threat intelligence can be integrated into incident response processes to improve the speed and effectiveness of response. This can be done by providing responders with access to the latest threat intelligence, which can help them to identify the root cause of the incident and to take the appropriate steps to mitigate the damage.
- Enhanced security monitoring: Threat intelligence can be integrated into security monitoring systems to enhance the visibility of threats. This can be done by providing security analysts with access to the latest threat intelligence, which can help them to identify suspicious activity and to take the appropriate steps to investigate and mitigate the threat.
- Vulnerability management: Threat intelligence can be integrated into vulnerability management processes to identify and prioritize vulnerabilities that are most likely to be exploited by attackers. This can be done by using threat intelligence to identify vulnerabilities that are being actively exploited by attackers or that are known to be targeted by attackers.
Integrating threat intelligence into security systems and processes is essential for organizations to maintain a strong security posture. By incorporating threat intelligence into their security systems and processes, organizations can improve their ability to identify, detect, and respond to threats in a timely and effective manner.
Detection
Detection is a critical aspect of threat intelligence integration. It involves identifying threats based on integrated threat intelligence in order to take appropriate action to mitigate these threats and reduce their impact on the organization.
- Automated threat detection: Threat intelligence can be integrated into security systems to automate the detection of threats. This can be done by using threat intelligence feeds to identify malicious IP addresses, URLs, and file hashes. When a security system detects a threat, it can automatically take action, such as blocking the threat or quarantining the infected system.
- Improved incident response: Threat intelligence can be integrated into incident response processes to improve the speed and effectiveness of response. This can be done by providing responders with access to the latest threat intelligence, which can help them to identify the root cause of the incident and to take the appropriate steps to mitigate the damage.
- Enhanced security monitoring: Threat intelligence can be integrated into security monitoring systems to enhance the visibility of threats. This can be done by providing security analysts with access to the latest threat intelligence, which can help them to identify suspicious activity and to take the appropriate steps to investigate and mitigate the threat.
- Vulnerability management: Threat intelligence can be integrated into vulnerability management processes to identify and prioritize vulnerabilities that are most likely to be exploited by attackers. This can be done by using threat intelligence to identify vulnerabilities that are being actively exploited by attackers or that are known to be targeted by attackers.
Detection is a critical aspect of threat intelligence integration. By identifying threats based on integrated threat intelligence, organizations can take appropriate action to mitigate these threats and reduce their impact on the organization.
Response
Threat intelligence integration plays a vital role in enabling organizations to respond effectively to threats and mitigate their potential impact. By providing access to timely and actionable threat intelligence, organizations can make informed decisions and take appropriate actions to protect their assets and infrastructure.
- Rapid Response: Threat intelligence integration facilitates rapid response to threats by providing real-time visibility into the threat landscape. Security teams can leverage threat intelligence to quickly identify and prioritize threats, enabling them to respond swiftly and effectively.
- Automated Mitigation: Threat intelligence can be integrated with security systems to automate mitigation actions. For example, organizations can configure their firewalls to automatically block IP addresses associated with malicious activity or quarantine infected systems based on threat intelligence indicators.
- Targeted Remediation: Threat intelligence enables organizations to focus their remediation efforts on the most critical threats. By understanding the specific tactics, techniques, and procedures (TTPs) used by attackers, organizations can prioritize vulnerabilities and implement targeted remediation measures.
- Intelligence-Driven Incident Response: Threat intelligence integration enhances incident response by providing context and insights into the nature and scope of an attack. This enables incident responders to make informed decisions, allocate resources efficiently, and develop tailored response strategies.
In summary, threat intelligence integration empowers organizations to respond to threats in a proactive, timely, and effective manner. By leveraging threat intelligence, organizations can minimize the impact of threats, protect their assets, and maintain a strong security posture.
Prevention
Threat intelligence integration plays a crucial role in enabling organizations to prevent future threats by providing insights into the tactics, techniques, and procedures (TTPs) used by attackers. By understanding the threat landscape and the methods employed by malicious actors, organizations can proactively strengthen their defenses and mitigate potential risks.
- Identifying Emerging Threats: Threat intelligence integration allows organizations to identify emerging threats and trends in the cybersecurity landscape. By analyzing threat intelligence feeds and reports, organizations can stay informed about the latest vulnerabilities, malware campaigns, and attack vectors, enabling them to take proactive measures to protect their systems.
- Proactive Vulnerability Management: Threat intelligence can be leveraged to prioritize and address vulnerabilities in an organization’s systems. By identifying vulnerabilities that are actively exploited by attackers, organizations can prioritize patching and remediation efforts, reducing the likelihood of successful cyberattacks.
- Security Configuration Optimization: Threat intelligence can provide insights into the misconfigurations and security weaknesses that attackers often target. Organizations can use this information to optimize their security configurations, harden their systems, and reduce the attack surface available to malicious actors.
- Employee Awareness and Training: Threat intelligence can be used to develop targeted training programs for employees, raising awareness about potential threats and phishing attempts. By educating employees about the latest threats and social engineering techniques, organizations can reduce the risk of successful attacks.
In summary, threat intelligence integration is essential for organizations to prevent future threats by providing valuable insights into the tactics and motivations of attackers. By leveraging threat intelligence, organizations can proactively strengthen their defenses, mitigate risks, and maintain a strong security posture.
Threat intelligence integration FAQs
Threat intelligence integration is a critical aspect of cybersecurity that involves collecting, analyzing, and sharing information about threats to an organization’s assets. Here are some frequently asked questions about threat intelligence integration:
Question 1: What are the benefits of threat intelligence integration?
Answer: Threat intelligence integration provides numerous benefits, including improved situational awareness, faster response times, enhanced security posture, and the ability to identify and prevent future threats.
Question 2: What are the key steps involved in threat intelligence integration?
Answer: The key steps involved in threat intelligence integration are collection, analysis, sharing, integration, detection, response, and prevention.
Question 3: How can threat intelligence integration help organizations prevent future threats?
Answer: Threat intelligence integration provides insights into the tactics, techniques, and procedures (TTPs) used by attackers, enabling organizations to proactively strengthen their defenses, mitigate risks, and prevent future threats.
Question 4: How does threat intelligence integration improve incident response?
Answer: Threat intelligence integration enhances incident response by providing context and insights into the nature and scope of an attack. This enables incident responders to make informed decisions, allocate resources efficiently, and develop tailored response strategies.
Question 5: What are some common challenges associated with threat intelligence integration?
Answer: Common challenges associated with threat intelligence integration include data overload, lack of skilled personnel, and the need for effective collaboration and information sharing.
Question 6: How can organizations overcome the challenges of threat intelligence integration?
Answer: Organizations can overcome the challenges of threat intelligence integration by implementing a structured approach, investing in training and personnel development, and fostering collaboration and information sharing within the organization and across industry peers.
In summary, threat intelligence integration is a crucial aspect of cybersecurity that enables organizations to identify, prevent, and respond to threats effectively. By understanding the key benefits, steps involved, and common challenges associated with threat intelligence integration, organizations can harness its full potential to protect their assets and maintain a strong security posture.
Now that we have covered these frequently asked questions, let’s move on to the next section of this article, which will provide a deeper dive into the benefits of threat intelligence integration.
Threat intelligence integration tips
Threat intelligence integration is a critical aspect of cybersecurity that involves collecting, analyzing, and sharing information about threats to an organization’s assets. Here are some tips to help organizations effectively integrate threat intelligence into their security strategies:
Tip 1: Establish a clear threat intelligence strategy
Organizations should define their threat intelligence goals and objectives, identify the sources of threat intelligence, and establish a process for collecting, analyzing, and sharing threat intelligence.
Tip 2: Invest in the right tools and technologies
Organizations should invest in the right tools and technologies to support threat intelligence integration, such as threat intelligence platforms, security information and event management (SIEM) systems, and threat detection and response tools.
Tip 3: Build a skilled threat intelligence team
Organizations should build a team of skilled threat intelligence analysts who have the expertise to collect, analyze, and interpret threat intelligence.
Tip 4: Foster collaboration and information sharing
Organizations should foster collaboration and information sharing within the organization and across industry peers to enhance their threat intelligence capabilities.
Tip 5: Continuously monitor and evaluate threat intelligence
Organizations should continuously monitor and evaluate their threat intelligence program to ensure that it is meeting their needs and adapting to the evolving threat landscape.
Tip 6: Use threat intelligence to improve security decision-making
Organizations should use threat intelligence to inform their security decision-making, such as prioritizing vulnerabilities, allocating resources, and developing security strategies.
Tip 7: Use threat intelligence to enhance incident response
Organizations should use threat intelligence to enhance their incident response capabilities, such as identifying the root cause of an incident, containing the damage, and preventing future incidents.
Tip 8: Use threat intelligence to prevent future threats
Organizations should use threat intelligence to prevent future threats by identifying emerging threats, prioritizing vulnerabilities, and implementing proactive security measures.
By following these tips, organizations can effectively integrate threat intelligence into their security strategies and gain a competitive advantage in the fight against cyber threats.
In conclusion, threat intelligence integration is essential for organizations to protect their assets and maintain a strong security posture. By implementing these tips, organizations can harness the full potential of threat intelligence and stay ahead of the evolving threat landscape.
Threat intelligence integration
Threat intelligence integration is a crucial aspect of cybersecurity that enables organizations to identify, prevent, and respond to threats effectively. By collecting, analyzing, and sharing information about threats, organizations can gain a deeper understanding of the threat landscape and make more informed decisions to protect their assets.
This article has explored the key benefits, steps involved, and common challenges associated with threat intelligence integration. We have also provided practical tips to help organizations effectively integrate threat intelligence into their security strategies.
In conclusion, threat intelligence integration is essential for organizations to maintain a strong security posture and protect themselves from the ever-evolving threat landscape. By embracing threat intelligence and implementing effective integration practices, organizations can proactively identify and mitigate threats, enhance their incident response capabilities, and prevent future attacks.
Youtube Video: